
Thematic video
Hide Your Secrets FOREVER! - Erasing Data SecurelySafe & Found
Safe & Found is a family location application, which allows the user to be always connected with various devices. With Safe & Found, the user can create an account with up to 5 mobile devices and use parental controls to restrict phone usage and/or control the use of other applications (“Safe & Found App” or “Safe & Found Service”). These Terms and Conditions apply to your use of and access to the Safe & Found Secure eraser android Activators Patch (“Safe & Found Terms”). Your use of and access to the Safe & Found Service is governed by Sprint’s General Terms and Conditions of Service (“Ts&Cs”); the information collected and used by the Safe & Sound Service is described in its Privacy Notice, also available within the Safe & Found App; as well as any other documents or materials that we provide or refer you to as described in the Ts&Cs (collectively, “Agreement”). By using the Safe & Found Service, you are agreeing to or accepting these Safe secure eraser android Activators Patch Found Terms and you acknowledge that you have read and understand this Agreement, agree to its terms, and specifically consent to the collection of information as described in the Safe & Sound Privacy Notice.
THE SAFE & FOUND APP IS NOT INTENDED FOR USE BY PERSONS UNDER THE AGE OF 13. IF YOU ARE UNDER 13 YEARS OLD, YOU MAY NOT USE THE SAFE & FOUND APP OR PROVIDE SPRINT WITH ANY PERSONALLY IDENTIFIABLE INFORMATION. IF YOU ARE 13 OR OLDER BUT NOT OF LEGAL AGE OR OTHERWISE WITHOUT CAPACITY TO ENTER INTO A CONTRACT, YOU SHOULD REVIEW THESE TERMS AND CONDITIONS WITH YOUR PARENT OR GUARDIAN TO MAKE Free audio converter premium crack THAT YOU AND YOUR PARENT OR GUARDIAN UNDERSTAND THESE SAFE & FOUND TERMS.
For purposes of interpreting secure eraser android Activators Patch Safe & Found Terms and the Ts&Cs with respect to the Safe & Found Service, the Safe & Found Service are included in the definition of “Services” in the Ts&Cs. Capitalized terms used and not defined in these Safe & Found Terms are used as defined in the Ts&Cs.
Sprint may modify the Safe & Found Service, the Safe & Found Terms, and the Ts&Cs at any time in its sole discretion. When and how Sprint will provide you notice of these changes is contained in the Ts&Cs or will otherwise be communicated to you. Your continued use of the Safe & Found Service following any change will constitute your acceptance of and agreement to be bound by the secure eraser android Activators Patch Agreement. If you do not agree with the modifications, your sole and exclusive remedy is to stop using the Safe & Found Service.
1. Mandatory Arbitration. As detailed in the Ts&Cs, you and Sprint agree to a mandatory arbitration provision that provides that (except for matters properly brought to small claims court) any claim, controversy, or dispute of any kind between you and must be resolved by final and binding arbitration on an individual and not a class-wide or consolidated basis.
2. Consent to Electronic and Email Communications. By creating an account for the Safe & Found Service, you consent to receiving text messages (SMS) related to the Safe & Found Service sent to the mobile number you enter as part of the account creation process. If you enter any other mobile numbers to invite them to join your family, you represent that the owners and/or authorized users of those mobile numbers have also provided their consent to receive the relevant text messages from us. You agree to electronic invoice delivery via email, confirm your ability to access your invoice online, and understand that you can change electronic delivery at any time. You also agree that you will promptly provide Sprint with an updated email address if it changes, secure eraser android Activators Patch. Sprint may use the email address that you provide to communicate with you about the Safe & Found Service. Sprint may also use your email address to tell you about Sprint products and services unless you have asked not to receive marketing emails from Sprint.
3. Electronic Signature and Disclosure Consent Notice. You agree to the use of electronic documents and records in connection with your registration for Safe & Found Service and all future documents and records in connection with Safe & Found Service—including without limitation this electronic signature and disclosure notice—and that this use satisfies any requirement that we provide you these documents and their content in writing. If you do not agree, do not accept this Agreement. You have the right to receive a paper copy of all documents and records. You may (i) obtain a paper copy of any document or record (free of charge), (ii) withdraw your consent to the use of electronic documents and records, or (iii) update your contact information by calling Customer Care at 866-275-1411 or at sprint.com. Your clicking on the “I accept” button indicates your signature and your acceptance of this notice.
4. How Does Safe & Found Work? With Safe & Found, you can see your “family” devices on a private map, inform others you’re in need of assistance, activate parental controls, and more. With Safe & Found you can create a family account with up to 5 family members and protect everyone with the following features: (a) Define safety areas and be automatically alerted when family members’ devices move in or out of these areas; (b) Locate family members’ devices in real time; (c) Send a Panic Alert to all members of your Safe & Found account; (d) Restrict calls to/from your family devices (iOS only), (e)control when apps can be used, (f) filter URLs and (g) find, (h) ring, (i) lock and (j) wipe (Android only) any family device if lost or stolen.
5. Actions Safe & Found Enables. Safe & Found allows users to respond to on demand location requests, remotely lock family member devices, remotely ring family member devices, remotely wipe family member devices, and remotely request family member on demand location. Safe & Found also has parental controls that allow a user to restrict access to applications on demand, respond to app restrictions on demand authorization requests, secure eraser android Activators Patch, provide time based apps restrictions support, calls restrictions support, manage family member general apps restrictions, manage family member apps restrictions (individually per app), manage family member call restrictions, and filter URLs.
6. Limitations. Due to limitations enforced by the iOS operating system, Safe & Found cannot guarantee that location/status information will be sent every 30 minutes to the server. To secure eraser android Activators Patch the impact of this limitation, secure eraser android Activators Patch, Safe & Found also relies on geo-fencing, location-based services, and location changes events that occur on the device to wake up and opportunistically send location/status information to the server. Nevertheless, the effectiveness of this approach ultimately depends on whether the device is moving or not. Please read the Safe & Found FAQs for more information about how Safe & Found works.
7. No Improper or Illegal Use. You agree that your use of the Safe & Found App will be solely for your lawful, personal use and for no other purpose. You will only request location information for devices assigned to your account, in the possession of individuals under your legal supervision, custody or control or for which you have obtained authorized consent to participate in the Service. Unlawful use of this service may carry criminal and/or civil penalties. You will not stalk, harass, harm, threaten or invade the privacy of any person. You also agree to follow all applicable laws and regulations.
8. Location Consent; Availability and Accuracy. By using the Safe & Secure eraser android Activators Patch App you understand that you have no expectation of privacy as to the location of your devices and you consent to Sprint's review of the location of the devices that are enabled as part of the Safe & Found App. Sprint does not guarantee the availability, accuracy, timeliness or completeness of location information and it may only be approximate, delayed or interrupted due to limiting factors such as coverage area, service type, location technology, device is disabled, on a call, sending messages, running applications, the battery is drained, atmospheric, environmental and geographic conditions, satellite limitations, cell site location and information or other network conditions. Location accuracy may also be limited in rural and other areas where the Sprint network coverage is limited.
9. Safety. Use caution if and when providing location information to others and only share location information with those you trust. Please do not endanger yourself and others by using the Safe & Found App while driving or engaging in any other activity that requires your full attention. The Safe & Found App is not a substitute for adult supervision. Always use caution when displaying and disseminating personally identifiable information about your device, yourself, others or the location of yourself or other users to anyone else.
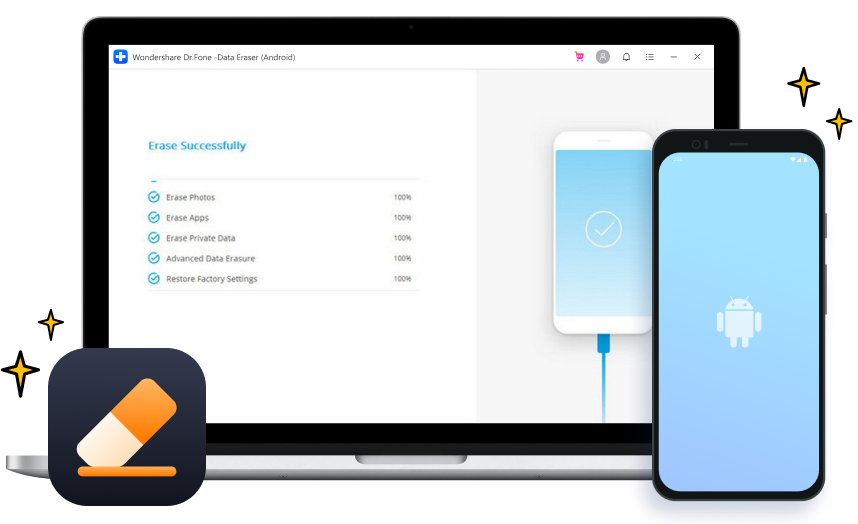
Permanently Erase Everything on Android
Dr.Fone - Data Eraser (Android)
- · Wipe your Android completely and permanently
- · Erase photos, contacts, messages, call logs and all private data
- · Support all Android devices available in the market
- · Simple, click-through process
try it freebuy now
Watch the video


Secure
It's secure to use Dr.Fone to erase data on Android because all data will erase with Military Grade Algorithm

Efficient
This Android data eraser helps you render your data completely unreadable and then clean up the whole disk completely.

Fast
One-click to wipe Android phone permanently with Android Data Eraser and protect your privacy.

Erase All Kinds of Personal Data
Zemana AntiMalware Premium 3.2.28 Full Crack + Serial Key {Lifetime} This Android data eraser is fully compatible with all Android devices, and supports erasing of all file types like photos, secure eraser android Activators Patch, contacts, messages, call logs, social app data, etc. One click to wipe an Android phone, and all privacy data are eliminated. Plan to sell, donate, or give out your Android phone? Erasing Android is your must-have step.
100% Wipe Data
This Android data eraser helps you render your data completely unreadable and then cleans up the whole disk. Even top-level hackers in the world have no means to recover a single bit from your erased Android. secure eraser android Activators Patch src="https://images.wondershare.com/drfone/product-2021/data-eraser/secure.png" alt="wipe data">
Steps for Using Data Eraser
The Android data eraser supports all available Android devices in the market. No matter you have Samsung, HTC, Sony, Motorola, Google Nexus, LG, or ZTE, etc, secure eraser android Activators Patch. and what Android version your phone is running on, This Android data eraser helps you erase everything on the phone permanently, secure eraser android Activators Patch.
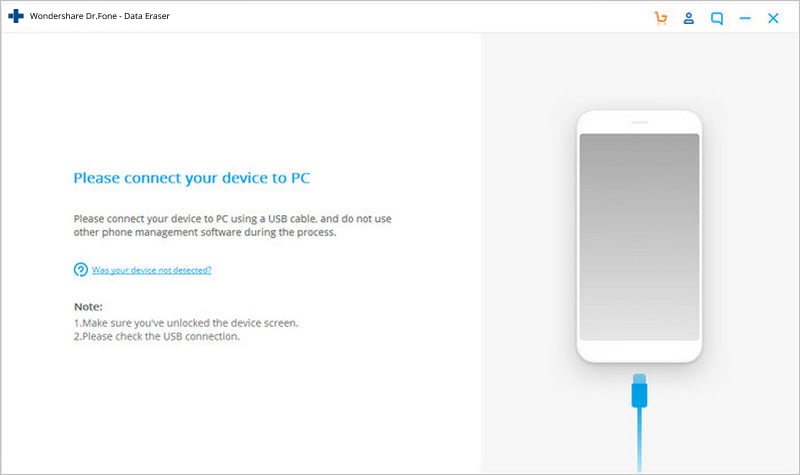
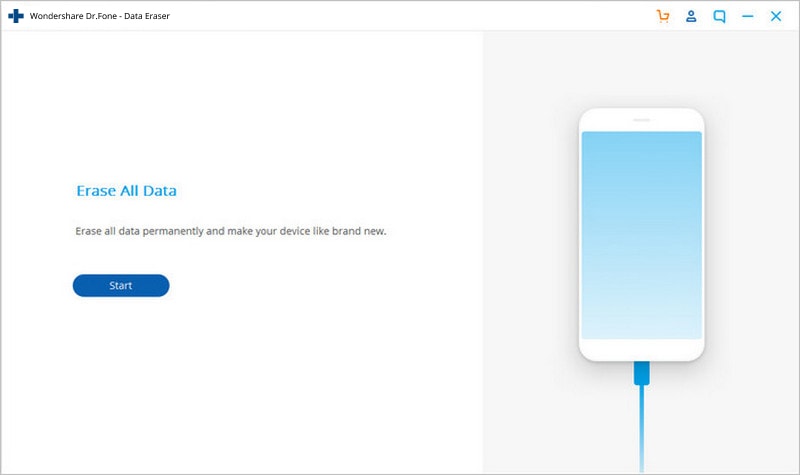
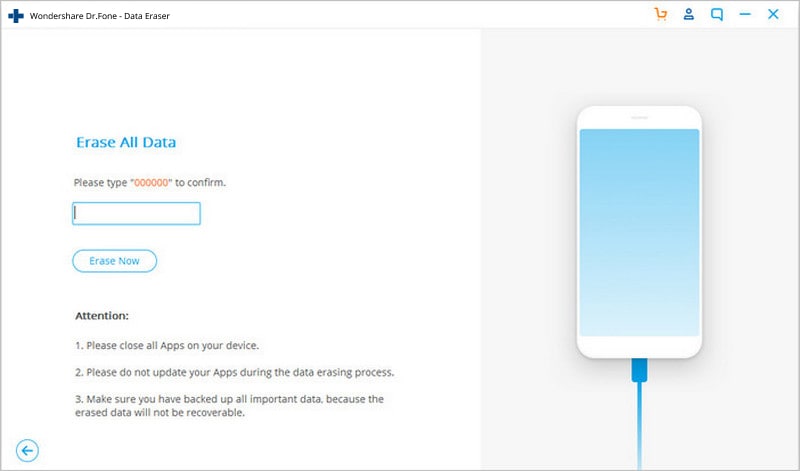
01 Connect your Android.
02 Mobikin Doctor Free Download erasing Android.
03 Complete erasing Android.
View Detailed Guide
secure eraser android Activators Patch Tech Specs
CPU
1GHz (32 bit or 64 bit)
RAM
256 MB or more of RAM (1024MB Recommended) secure eraser android Activators Patch secure eraser android Activators Patch
Hard Disk Space secure eraser android Activators Patch
200 MB and above free space
softmaker office 2018 mac crack Android
Android 2.1 and up to the latest
nox app apk Computer OS
Windows: Win 11/10/8.1/8/7
Mac: 12 (macOS Monterey), 11 (macOS Big Sur), 10.15 (macOS Catalina), 10.14 (macOS Mojave), Mac OS X 10.13 (High Sierra), 10.12(macOS Sierra), 10.11(El Capitan), 10.10 (Yosemite), 10.9 (Mavericks), or 10.8
Android Data Eraser FAQs
- Does Dr.Fone - Data Eraser (Android) completely erase all data on the phone?
Yes, this Android data eraser completely and permanently clean up all the personal secure eraser android Activators Patch on the phone, including contacts, messages, photos, call logs, calendars, app and app data, etc.
- What should I pay attention to when I use Dr.Fone - Data Eraser (Android)?
Traditional factory data reset does not clean your personal data on the phone 100%. Android Data Eraser helps you wipe the Android device clean and get it back to factory settings. Please do not disconnect the phone or open any other Android management software during the whole process. And at the end, follow the instruction on Android Data Eraser to perform a factory reset on your phone.
- What Android devices does Android Data Eraser support?
secure eraser android Activators Patch Currently, this Android data eraser supports all Android devices available in the market. And it will quickly support more new Android devices once they are released. But it doesn't work on Android devices with an unresponsive touch screen.
- What happens when you factory reset your phone?
When you factory reset your Android, the disk inside your Android is formatted. This does not mean that all the data on the disk are erased, but that all the indexes to files like photos, videos, docs, messages, etc. are canceled and these original files are ready to be overwritten. But, as long as you do not use the phone, the original files won't be overwritten, and they are always recoverable with special tools.
latest post

How do I Get my Old WhatsApp Account on My New Phone? secure eraser android Activators Patch
Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.

How do I Get my Old WhatsApp Account on My New Phone?
secure eraser android Activators Patch Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.

How do I Get my Old WhatsApp Account on My New Phone?
Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.

How do I Get my Old WhatsApp Account on My New Phone?
Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.

How do I Get my Old WhatsApp Account on My New Phone? secure eraser android Activators Patch
Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.

How do I Get my Old WhatsApp Account on My New Phone?
Do you want to get your move your WhatsApp Account to your new phone? Here's how to do it.
Our Customers Are Also Downloading
Android Enterprise feature list
This page lists the complete set of Android Enterprise features.
If you intend to manage more than 1000 devices, your EMM solution must support all the standard features (star) of at least one solution set before it can be made commercially available. EMM solutions that pass standard feature verification are listed in Android's Enterprise Solutions Directory as offering a Standard Management Set.
An extra set of advanced features is available for each solution set. These features are denoted in each solution set page: work profile, fully managed device, and dedicated device. EMM solutions that pass advanced feature verification are listed in Android's Enterprise Solutions Directory as offering an Advanced Management Set.
Key
| star standard feature | star_border optional feature | remove_circle_outline not applicable |
1. Device provisioning
1.1. DPC-first work profile provisioning
After downloading Android Device Policy from Google Play, users can provision a work profile.
1.1.1. The EMM provides an IT admin with a QR code or activation code to support this provisioning method (go to enrolling and provisioning a device).
1.2. DPC-identifier device provisioning
Entering "afw#" in the device's setup wizard provisions a fully managed or dedicated device.
1.2.1. The EMM provides an IT admin with a QR code or activation code to support this provisioning method (go to enrolling and provisioning a device).
1.3. NFC device provisioning
IT admins can "bump" new or factory-reset devices with an NFC to to provision a device, according to the implementation guidelines defined in the Play EMM API developer documentation.
1.3.1. EMMs must use NFC Forum Type 2 Tags with at least 888 bytes of memory. Provisioning must use provisioning extras to pass non-sensitive registration details such as server IDs and enrollment IDs to a device. Registration details shouldn't include sensitive information, such as passwords or certificates.
1.4. QR code device provisioning
The EMM's console can generate a QR code that IT admins can scan to provision a fully-managed or dedicated device, according to implementation guidelines defined in the Android Management API developer documentation.
1.4.1. The QR code must use provisioning extras to pass non-sensitive registration details (such as server IDs, enrollment IDs) to a device. Registration details must not include sensitive information, such as secure eraser android Activators Patch or certificates.
1.5. Zero-touch enrollment
IT admins can preconfigure devices purchased from authorized resellers and manage them using your EMM console.
1.5.1. IT admins can provision company-owned devices using the zero-touch enrollment method, outlined in Zero-touch enrollment for IT admins.
1.5.2. When a device is first turned on, the device is automatically forced into the settings defined by the IT admin.
1.6, secure eraser android Activators Patch. Advanced zero-touch provisioning
IT admins can automate much of the device enrollment process with zero-touch enrollment. Combined with sign-in URLs, IT admins can limit enrollment to specific accounts or domains, according to the configuration options offered by the EMM.
1.6.1. IT admins can provision a company-owned device using the zero-touch enrollment method.
1.6.2. This requirement is deprecated.
1.6.3. Using the sign-in URL, the EMM must ensure that unauthorized users can’t proceed with activation. At a minimum, activation must be locked down to users of a given enterprise.
1.6.4. Using the sign-in URL, the EMM must make it possible for IT admins to pre-populate registration details (for instance server IDs, enrollment IDs) aside from unique user or device information (for instance username/password, activation token), so that users don't have to enter details when activating a device.
- EMMs must not include sensitive information, such as passwords or certificates, in the zero-touch enrollment's configuration.
1.7, secure eraser android Activators Patch. Google Account work profile provisioning
The Android Management API doesn't support this feature.
1.8 Google Account device provisioning
The Android Management API doesn't support this feature.
1.9. Direct zero-touch configuration
IT admins can use the EMM's console to set up zero-touch devices using the zero-touch iframe.
1.10. Work profiles on company-owned devices
EMMs can enroll company-owned devices that have a work profile by setting AllowPersonalUsage.
1.10.1. IT admins can provision a device as a work profile on a company-owned device using a QR code or zero-touch enrollment.
1.10.2. IT admins can set compliance actions for work profiles on company-owned devices through PersonalUsagePolicies.
1.10.3. IT admins can deactivate the camera in either the work profile or the entire device through PersonalUsagePolicies.
1.10.4. IT admins can deactivate screen capture in either the work profile or an entire device through PersonalUsagePolicies.
1.10.5. IT admins can set an allowlist or blocklist of applications that can or cannot be installed in the personal profile through PersonalApplicationPolicy.
1.10.6. IT admins can relinquish management of a company-owned device by removing the work profile or wiping the entire device.
2. Device security
2.1. Device secure eraser android Activators Patch challenge
IT admins can set and enforce a device security challenge (PIN/pattern/password) from a predefined selection of 3 complexity levels on managed devices.
2.1.1 Policy must enforce settings managing device security challenges (parentProfilePasswordRequirements for work profile, passwordRequirements for fully managed and dedicated devices).
2.1.2. The password complexity should map to the following password complexities:
- PASSWORD_COMPLEXITY_LOW - pattern or pin with repeating (4444) or ordered (1234, 4321, 2468) sequences.
- PASSWORD_COMPLEXITY_MEDIUM - PIN with no repeating (4444) or ordered (1234, 4321, 2468) sequences, alphabetic, or alphanumeric password with a length of at least 4
- PASSWORD_COMPLEXITY_HIGH - PIN with no repeating (4444) or ordered (1234, 4321, 2468) sequences and a length of at least 8 or alphabetic or alphanumeric passwords with a length of at least 6
2.1.3. Additional password restrictions can also be enforced as legacy settings on company-owned devices.
2.2 Work security challenge
IT admins can set and enforce a security challenge for apps and data in the work profile that is separate and has different requirements from the device security challenge (2.1.).
2.2.1. Policy must enforce the security challenge for the work profile.
- By default, IT admins should set restrictions only for the work profile if no scope is specified
- IT admins can set secure eraser android Activators Patch device-wide by specifying the scope (see requirement 2.1)
2.2.2. The password complexity should map to the following predefined password complexities:
- PASSWORD_COMPLEXITY_LOW - pattern or pin with repeating (4444) or ordered (1234, 4321, 2468) sequences.
- PASSWORD_COMPLEXITY_MEDIUM - PIN with no repeating (4444) or ordered (1234, 4321, 2468) sequences, alphabetic, or alphanumeric password with a length of at least 4
- PASSWORD_COMPLEXITY_HIGH - PIN with no repeating (4444) or ordered (1234, secure eraser android Activators Patch, 4321, 2468) sequences and a length of at least 8 or alphabetic or alphanumeric passwords with a length of at least 6
2.2.3. Additional password restrictions can also be enforced as legacy settings
2.3. Advanced passcode management
IT admins can set up advanced password settings on devices.
2.3.1. [intentionally blank]
2.3.2. secure eraser android Activators Patch blank]
2.3.3. The following password lifecycle settings can be set for each lock screen available on a device:
- [intentionally blank]
- [intentionally blank]
- Maximum failed passwords for wipe: Specifies the number of times users can enter an incorrect password before corporate data is wiped from the device. IT admins must be able to turn off this feature.
2.3.4. (Android 8.0+) Strong Authentication required timeout: a strong authentication passcode (such as PIN or password) must be input after a timeout period set by an IT admin. After the timeout period, non-strong authentication methods (such as fingerprint, face unlock) are turned off until the device is unlocked with a strong authentication passcode.
2.4. Smart lock management
IT admins can manage whether trust agents in Android's Smart Lock feature are permitted to extend device unlock up to four hours.
2.4.1. IT admins can disable trust agents on the device.
2.5. Wipe and lock
IT admins can use the EMM's console to remotely lock and wipe work data from a managed device.
2.5.1. Devices must be locked using the Android Management API.
2.5.2. Devices must secure eraser android Activators Patch wiped using the Android Management API.
2.6. Compliance enforcement
If a device is not compliant with security policies, compliance rules put in place by the Android Management API automatically restrict use of work data.
2.6.1. At minimum, the security policies enforced on a device must include password policy.
2.7. Default security policies
EMMs must enforce the specified security policies on devices by default, without requiring IT admins to set up or customize any settings in the EMM's console. EMMs are encouraged (but not required) to not allow IT admins to change the default state of these security features.
2.7.1. Installing apps from unknown sources must be blocked, including apps installed on the personal side of any Android 8.0+ device with a work profile. This subfeature is supported by default.
2.7.2. Debugging features must be blocked. This subfeature is supported by default.
2.8. Security policies for dedicated devices
No other actions are allowed for a locked down dedicated device.
2.8.1. Booting into safe mode must be turned off by default via policy (Go to ).
2.9. SafetyNet Support
SafetyNet is turned on by default. No extra implementation is required.
2.10. Verify Apps enforcement
IT admins can turn on Verify Apps on devices. Verify Apps scans apps installed on Android devices for harmful software before and after they're installed, helping to ensure that malicious apps can’t compromise corporate data.
2.10.1. Verify Apps must be turned on by default via policy (Go to ).
2.11. Direct Boot support
The Android Management API supports this feature by default. No extra implementation is required.
2.12. Hardware security management
IT admins can lock down hardware elements of a company-owned device to ensure data-loss prevention.
2.12.1. IT admins can block users from mounting physical external media via policy (go to ).
2.12.2. IT admins can block users from sharing data from their device using NFC beam via policy (go to ).
2.12.3. IT admins can block users from transferring files over USB via policy (go to ).
2.13. Enterprise security logging
The Android Management API doesn't currently support this feature.
3. Account and app management
3.1. Managed Google Play Accounts enterprise enrollment
IT admins can create a managed Google Play Accounts enterprise—an entity that allows managed Google Play to distribute apps to devices. The following enrollment stages must be integrated into the EMM's console:
3.1.1. Enroll a managed Google Play Accounts enterprise using the Android Management API.
3.2. Managed Google Play Account provisioning
The EMM can silently provision enterprise user accounts, called managed Google Play accounts. These accounts identify managed users and allow unique, per-user app distribution rules.
3.2.1. Managed Google Play Accounts (user accounts) are automatically created when devices are provisioned.
The Android Management API supports this feature by default, secure eraser android Activators Patch. No extra implementation is required.
3.3. Managed Google Play device account provisioning
The EMM can create and provision managed Google Play device accounts. Device accounts support silently installing apps from the managed Google Play Store, and are not tied secure eraser android Activators Patch a single user. Instead, a device account is used to identify a single device to support app distribution rules per device in dedicated device scenarios.
3.3.1. Managed Google Play Accounts are automatically created when devices are provisioned.
The Android Management API supports this feature by default. No extra implementation is required.
3.4. Managed Google Play Account provisioning for legacy devices
This feature is deprecated.
3.5. Silent app distribution
IT admins can silently distribute work apps on devices without any user interaction.
3.5.1. The EMM's console must use the Android Management API to allow IT admins to install work apps on managed devices.
3.5.2. The EMM's console must use the Android Management API to allow IT admins to update work apps on managed devices.
3.5.3. The EMM's console must use the Android Management API to allow IT admins to uninstall apps on managed devices.
3.6. Managed configuration management
IT admins can view and silently set managed configurations for any app that supports managed configurations.
3.6.1. Movavi video editor crack 32 bit Free Activators EMM's console secure eraser android Activators Patch be able to retrieve and display the managed configuration settings of any Play app.
3.6.2, secure eraser android Activators Patch. The EMM's console must allow IT admins to set any configuration type (as defined by the Android Enterprise framework) for any Play app using the Android Management API.
3.6.3. The EMM's console must allow IT admins to set wildcards (such as $username$ or %emailAddress%) so that a single configuration for an app such as Gmail can be applied to multiple users.
3.7. App catalog management
The Android Management API supports this feature by default. No additional implementation is required.
3.8. Programmatic app approval
The EMM's console uses the managed Google Play iframe to support Google Play's app discovery and approval capabilities. IT admins can search for apps, approve apps, and approve new app permissions without leaving the EMM's console.
3.8.1. IT admins can search for apps and approve them within the EMM's console using the managed Google Play iframe.
3.9. Basic store layout management
The managed Google Play Store app can be used to install and update work apps. By default, the managed Google Play Store displays apps approved for a user in a single list. This layout is referred to as basic store layout.
3.9.1. The EMM's console should allow IT admins to manage the apps visible in an end user's basic store layout.
3.10. Advanced store layout configuration
3.10.1. IT admins can customize the store layout seen in the managed Google Play Store app.
3.11. App license management
This feature is deprecated.
3.12. Google-hosted private secure eraser android Activators Patch management
IT admins can update Google-hosted private apps through the EMM console instead of through the Google Play Console.
3.12.1. IT admins can upload new versions of apps that are already published privately to the enterprise using:
3.13. Self-hosted private app management
IT admins can set up and publish self-hosted private apps. Unlike Google-hosted private apps, Google Play does not host the APKs, secure eraser android Activators Patch. Instead, the EMM helps IT admins host APKs themselves, and helps protect self-hosted apps by ensuring they can only be installed when authorized by managed Google Play.
3.13.1. The EMM's console must help IT admins host the app APK, by offering both of the following options:
- Hosting the APK on the EMM's server. The server can be on-premise or cloud-based.
- Hosting the APK outside of the EMM's server, at the discretion of the enterprise. The IT admin must specify in the EMM console where the APK is hosted.
3.13.2. The EMM's console must generate an appropriate APK definition file using the provided APK and must guide IT admins through the publishing process.
3.13.3. IT admins can update self-hosted private apps, and the EMM's console can silently publish updated APK definition files using the Google Play Developer Publishing API.
3.13.4. The EMM's server serves download requests for the self-hosted APK that contains a valid JWT within the request's cookie, as verified by the private app's public key.
- To facilitate this process, the EMM's server must guide IT admins to download the self-hosted app's license public key from secure eraser android Activators Patch Play Google Developers Console, and upload this key to the EMM console.
3.14. EMM pull notifications
This feature is not applicable to the Android Management API. Set up Pub/Sub notifications instead.
3.15. API usage requirements
The EMM implements Android Management APIs at scale, secure eraser android Activators Patch, avoiding traffic patterns that could negatively impact enterprises’ ability to manage apps in production environments.
3.15.1. The EMM must adhere to the Android Management API usage limits. Not correcting behavior that exceeds these guidelines may result in suspension of API use, at Google's discretion.
3.15.2. The EMM should distribute traffic from different enterprises throughout the day, rather than consolidating enterprise traffic at specific or similar times. Behavior that fits this traffic pattern, such as scheduled batch operations for each device enrolled, may result in suspending API use, secure eraser android Activators Patch, at Google's discretion.
3.15.3. The EMM should not make consistent, secure eraser android Activators Patch, incomplete, or deliberately incorrect requests that secure eraser android Activators Patch no attempt to retrieve or manage actual enterprise data. Behavior that fits this traffic pattern may result in suspended API use, at Google's discretion.
3.16. Advanced managed configuration management
The EMM supports the following advanced managed configuration management features:
3.16.1. The EMM's console must be able to retrieve and display the up to four levels of nested managed configuration settings of any Play app, using:
3.16.2. The EMM's console must be able to retrieve and display any feedback returned by an app's feedback channel, when set up by an IT admin.
- The EMM's console must allow IT admins to associate a specific feedback item with the device and app it originated from.
- The EMM's console must allow IT admins to subscribe to alerts or reports of specific message types (such as error messages).
3.16.3, secure eraser android Activators Patch. The EMM’s console must only send values that either have a default value or are manually set by the admin using:
- The managed configurations iframe, or
- A custom UI.
3.17. Web app management
IT admins can create and distribute web apps in the EMM console.
3.17.1. The EMM console allows IT admins to distribute shortcuts to web apps using:
3.18. Managed Google Play Account lifecycle management
The EMM can create, update, and delete managed Google Play Accounts on behalf of IT admins, and automatically recover from account expiration.
This feature is supported by default. No extra EMM implementation is required.
3.19. Application track management
3.19.1. IT Admins can pull a list of track IDs set by a developer for a particular app
3.19.2. IT Admins can set devices to use a particular development track for an application.
3.20. Advanced application update management
IT admins can allow apps to be updated immediately or postpone them from being updated for 90 days.
3.20.1. IT admins can allow apps to use high-priority app updates to be updated when an update is ready. 3.20.2. IT admins can allow apps to have their app updates postponed for 90 days.
4. Device management
4.1. Runtime permission policy management
IT admins can silently set a default response to runtime permission requests made by work apps.
4.1.1. IT admins must be able to choose from the following options when setting a default runtime permission policy for their organization:
- prompt secure eraser android Activators Patch users to choose)
- allow
- deny
The EMM should enforce these settings via policy.
4.2. Runtime permission grant state management
After setting a default runtime permission policy (go to 4.1.), IT admins can silently set responses for specific permissions from any work app built on API 23 or above.
4.2.1. IT admins must be able to set the grant state (default, grant, or deny) of any permission requested by any work app built on API 23 or above. The EMM should enforce these settings via policy.
4.3. Wi-Fi configuration management
IT admins can silently provision enterprise Wi-Fi configurations on managed devices, including:
4.3.1. SSID, via policy.
4.3.2. Password, via policy.
4.4. Wi-Fi security management
IT admins can provision enterprise Wi-Fi configurations on devices that include the following advanced security features:
4.4.1. Identity
4.4.2. Certificates for client authorization
4.4.3. CA certificates
4.5. Advanced Wi-Fi management
IT admins can lock down Wi-Fi configurations on managed devices, to prevent users from creating configurations or modifying corporate configurations.
4.5.1. IT admins can lock down corporate Wi-Fi configurations via policy in either of the following configurations:
- Users cannot modify any Wi-Fi configurations provisioned by the EMM (go to ), but secure eraser android Activators Patch may add and modify their own user-configurable networks (for instance personal networks).
- Users cannot add or modify any Wi-Fi network on the device (go to ), limiting Wi-Fi connectivity to just those networks provisioned by the EMM.
4.6. Account management
IT admins can ensure that only authorized corporate accounts can interact with corporate data, for services such as SaaS storage and productivity apps, or email. Without this feature, users can add personal accounts to those corporate apps that also support consumer accounts, enabling them to share corporate data with secure eraser android Activators Patch personal accounts.
4.6.1. IT admins can prevent users from adding or modifying accounts (see ).
- When enforcing this policy on a device, secure eraser android Activators Patch, EMMs must set this restriction before provisioning is complete, to ensure users cannot circumvent this policy by adding accounts before the policy is enacted.
4.7. Workspace account management
The Android Management API doesn't support this feature.
4.8. Certificate management
Allows IT admins to deploy identity certificates and certificate authorities to devices to allow use of corporate resources.
4.8.1. IT admins can install user identity certs generated by their PKI on a per-user basis. The EMM's console must integrate with at least one PKI and distribute certificates generated from that infrastructure.
4.8.2. IT admins can install certificate authorities (see ) in the managed keystore.
4.9. Advanced certificate management
Allows IT admins to silently select the certificates that specific managed avast secureline vpn lifetime license should use. This feature also grants IT admins the ability to remove CAs and identity certs from active devices, and prevent users from modifying credentials stored in the managed keystore.
4.9.1. For any app distributed to devices, secure eraser android Activators Patch, IT admins can specify a certificate the app will be silently granted access during runtime. (This subfeature is not currently supported)
- Certificate selection must be generic enough to allow a single configuration that applies to all users, each of which may have a user-specific identity certificate.
4.9.2. IT admins can silently remove certificates from the managed keystore.
4.9.3. IT admins can silently uninstall a CA certificate. (This subfeature is not currently supported)
4.9.4. IT admins can prevent users from configuring credentials (go to ) in the managed keystore.
4.9.5. IT admins can pre-grant certificates for secure eraser android Activators Patch apps using ChoosePrivateKeyRule.
4.10. Delegated certificate management
IT admins can distribute a third-party certificate management app to devices and grant that app privileged access to install certificates into the managed keystore.
4.10.1. IT admins can specify a certificate management package (go to ) to be set as the delegated certificate management app.
- The EMM's may optionally suggest known certificate management packages, but must allow the IT admin to choose from the list of apps available for install, for applicable users.
4.11. Advanced VPN management
Allows IT admins to specify an Always On VPN to ensure that the data from specified managed apps will always go through a set-up Virtual Private Network (VPN). antivirus with crack download Free Activators this feature requires deploying a VPN client that supports both Always On and per-app VPN features.
4.11.1. IT admins can specify an arbitrary VPN package to be set as an Always On VPN.
- The EMM's console may optionally suggest known VPN packages that support Always On VPN, but can't restrict the VPNs available for Always On configuration to any arbitrary list.
4.11.2. IT admins can use managed configurations to specify the VPN settings for an app.
4.12. IME management
IT admins can manage what input methods (IMEs) can be set up for devices. Since the IME is shared across both work and personal profiles, blocking use of IMEs will prevent users from allowing those IMEs for personal use as well. IT admins may not, however, block use of system IMEs on work profiles (go to advanced IME management for more details).
4.12.1. IT admins can set up an IME allowlist (Go to ) of arbitrary length (including an empty list, which blocks non-system IMEs), which may contain any arbitrary IME packages.
- The EMM's console may optionally suggest known or recommended IMEs to include in the allowlist, but must allow IT admins to choose from the list of apps available for install, for applicable users.
4.12.2. The EMM must inform IT admins that system IMEs are excluded from management on devices with work profiles.
4.13. Advanced IME management
IT admins can manage what input methods (IMEs) users can set up on a device. Advanced IME management extends the basic feature by allowing IT admins to manage the use of system IMEs as well, which device manufacturer or carrier of the device typically provide.
4.13.1. IT admins can set up an IME allowlist (go to ) of arbitrary length (excluding an empty list, which blocks all IMEs including system IMEs), which may contain any arbitrary IME packages.
- The EMM's console may optionally suggest known or recommended IMEs to include in the allowlist, but must allow IT admins to choose from the list of apps available for install, for applicable users.
4.13.2. EMM must prevent IT admins from setting up an empty allowlist, as this setting will block all IMEs including system IMEs from being set up on the device.
4.13.3. EMM must ensure that if an IME allowlist does not contain system IMEs, the third-party IMEs are silently installed before the allowlist is applied on the device.
4.14. Accessibility services management
IT admins can manage what accessibility services users can allow on devices. Accessibility services are powerful tools for users with disabilities or those that are temporarily unable to fully interact with a device. However, they may interact with corporate data in ways that are non-compliant with corporate policy. This feature allows IT admins to turn off any non-system accessibility service.
4.14.1. IT admins can set up an accessibility service allowlist (go to ) of arbitrary length (including an empty list, which blocks non-system accessibility services), which may contain any arbitrary accessibility service package. When applied to a work profile, this affects both the personal profile and the work profile.
- Console may optionally suggest known or recommended accessibility services to include in the allowlist, but must allow IT admin to choose from the list of apps available for install, for applicable users.
4.15. Location Sharing management
IT admins can prevent users from sharing location data with apps in the work profile. Otherwise, the location setting in the work profile is configurable in Settings.
4.15.1. IT admins can disable location services (go to ) within the work profile.
4.16. Advanced Location Sharing management
IT admins can enforce a given Location Sharing setting on a managed device. This feature can ensure that corporate apps always have high accuracy location data. This feature can also ensure that extra battery is not consumed by restricting location settings to battery saving mode.
4.16.1, secure eraser android Activators Patch. IT admins can set the device location services to each of the following modes:
- High accuracy.
- Sensors only, for instance GPS, but not including network-provided location.
- Battery saving, which limits the update frequency.
- Off.
4.17. Factory reset protection management
Allows IT admins to protect company-owned devices from theft by ensuring unauthorized users can’t factory reset devices. If factory reset protection introduces operational complexities when devices are returned to IT, IT admins can turn off factory reset protection entirely.
4.17.1. IT admins can prevent users from factory resetting (go to ) their device from Settings.
4.17.2. IT admins can specify corporate unlock account(s) authorized to provision devices (go to ) after a factory reset.
- This account can be tied to an individual, or used by the entire enterprise to unlock devices.
4.17.3. IT admins can disable factory reset protection (go to0 ) for specified devices.
4.17.4. IT admins can start a remote device wipe that optionally wipes reset protection data, thus removing factory reset protection on the reset device.
4.18. Advanced app control
IT admins can prevent the user from uninstalling or otherwise modifying managed apps through Settings. For instance, secure eraser android Activators Patch, preventing force closing the app or clearing an app's data cache.
4.18.1. IT admins can block uninstall of any arbitrary managed apps, or all managed apps (go to ).
4.18.2. IT admins can prevent users from modifying application data (go to ) from Settings.
4.19. Screen capture management
IT admins can block users from taking screenshots when using managed apps. This setting includes blocking screen sharing apps and similar apps (such as Google Assistant) that leverage the system screenshot capabilities.
4.19.1. IT admins can prevent users from capturing screenshots (go to ).
4.20. Disable cameras
IT admins can turn off use of device cameras by managed apps.
4.20.1. IT admins can disable use of device cameras (go to ) by managed apps.
4.21. Network statistics collection
The Android Management API doesn't currently support this feature.
4.22. Advanced network statistics collection
The Android Management API doesn't currently support this feature.
4.23. Reboot device
IT admins can remotely restart managed devices.
4.23.1. IT admins can remotely reboot a managed device.
4.24. System radio management
Provides IT admins with granular management over system network radios and associated use policies via policy.
4.24.1. IT admins can turn off cell broadcasts sent by secure eraser android Activators Patch providers (go to ).
4.24.2. IT admins can prevent users from modifying mobile network settings in Settings (go to ).
4.24.3. IT admins can prevent users from resetting all network settings in Settings. (go to ).
4.24.4. IT admins can set up whether the device permits mobile data while roaming (go to ).
4.24.5. IT admins can set up whether the device can make outgoing phone calls, excluding emergency calls (go to ).
4.24.6. IT admins can set up whether the device can send and receive text messages (go to ).
4.24.7. IT admins can prevent users from using their device as a portable hotspot by tethering (go to ).
4.24.8. IT admins can set the Wi-Fi timeout to default, while plugged in, or never. (The Android Management API doesn't support this subfeature)
4.24.9. IT admins can prevent users from setting up or modifying existing Bluetooth connections (go to ).
4.25. System audio management
IT admins can silently control device audio features, including muting the device, preventing users from modifying volume settings, and preventing users from unmuting the device microphone.
4.25.1. IT admins can silently mute managed devices (go to ).
4.25.2. IT admins can prevent users from modifying device volume settings (go to ). This also mutes the devices.
4.25.3. IT admins can prevent users from unmuting the device microphone (go to ).
4.26. System clock management
IT admins can manage device clock and time zone settings, and prevent users from modifying automatic device settings.
4.26.1. IT admins can enforce system auto time and auto time zone, secure eraser android Activators Patch, preventing the user from setting the date, time, and time zone of the device.
4.27. Advanced dedicated device features
For dedicated devices, IT admins can manage the following features via policy to support various kiosk use cases.
4.27.1. IT admins can turn off the device keyguard (go to ).
4.27.2. IT admins can turn off the device status bar, blocking notifications and quick settings (go to ).
4.27.3. IT admins can force the device screen to remain on while the device is plugged in (go to ).
4.27.4, secure eraser android Activators Patch. IT admins can prevent the following system UIs from being displayed (go to ):
- Toasts
- Phone activities (such as incoming calls) and priority phone activities (such as ongoing calls)
- System alerts, system errors, and system overlays.
4.27.5. IT admins can allow the system recommendation for apps to skip their user tutorial and other introductory hints on first start-up (go to ).
4.28. Delegated scope management
IT admins are able to delegate extra privileges to individual packages.
4.28.1. IT admins can manage the following scopes:
- Certificate installation and management
- Managed configurations management
- Blocking uninstallation
- Permission policy and permission grant state
- Package access state
- Enabling system apps
4.29. Enrollment-specific ID Support
Starting in Android 12, secure eraser android Activators Patch, work profiles will no longer have access to hardware-specific identifiers. IT admins can follow the lifecycle of a device with a work profile through the enrollment-specific ID, which will persist through factory resets
4.29.1. IT admins can obtain an enrollment-specific ID
4.29.2. This enrollment-specific ID must persist through a factory reset
5. Device usability
5.1. Managed provisioning customization
IT admins can modify the default setup flow UX to include enterprise-specific features. Optionally, IT admins can display EMM-provided branding during provisioning.
5.1.1. IT admins can customize the provisioning process by specifying enterprise-specific Terms of Service and other disclaimers (go to ).
5.1.2, secure eraser android Activators Patch. IT admins can deploy non-configurable, secure eraser android Activators Patch, EMM-specific Terms of Service and other disclaimers (go to ).
- EMMs may set their non-configurable, EMM-specific customization as the default for deployments, but must allow IT admins to set up their own customization.
5.1.3 has been deprecated for the enterprise resource on Android 10 and above.
5.2. Enterprise customization
The Android Management API doesn't support this feature.
5.3. Advanced enterprise customization
The Android Management API doesn't support this feature.
5.4. Lock screen messages
IT admins can set a custom message that's always displayed on the device lock screen, and does not require device unlock to be viewed.
5.4.1. IT admins can set a custom lock screen message (go to ).
5.5. Policy transparency management
IT admins can customize the help text provided to users when they attempt to modify managed settings on their device, or deploy an EMM-supplied generic support message. Both short and long support messages can be customized, and are displayed in instances such as attempting to uninstall a managed app for which an IT admin has already blocked uninstallation.
5.5.1. IT admins can customize short and long user-facing vMix Pro 24.0.0.63 Crack With Serial Key Free Download [2021] messages.
5.5.2. IT admins can deploy non-configurable, EMM-specific, short and long support messages (go to and in ).
- EMM may set their non-configurable, EMM-specific support messages as the default for deployments, but must allow IT admins to set up their own messages.
5.6. Cross-profile contact management
5.6.1. IT admins can disable displaying work contacts in personal profile contact searches and incoming calls.
5.6.2. IT admins can disable bluetooth contact sharing of work contacts, for instance hands-free calling in cars or headsets.
5.7. Cross-profile data management
Allows IT admins to manage the types of data that can be shared between the work and personal profiles, allowing admins to balance usability and data security according to their requirements.
5.7.1. IT admins can configure cross-profile data sharing policy so that personal apps can resolve intents from the work profile, such as sharing intents or web links.
5.7.2. Work widget management is not yet available in the Android Management API.
5.7.3. IT admins can control the ability to copy/paste between the work and personal profiles.
5.8. System update policy
IT admins can set up and apply over-the-air (OTA) system updates devices.
5.8.1. The EMM's console allows IT admins to set the following OTA configurations:
- Automatic: Devices receive OTA updates when they become available.
- Postpone: IT admins must be able to postpone OTA update for up to 30 days.
- Windowed: IT admins must be able to schedule OTA updates within a daily maintenance window.
5.8.2. OTA configurations are applied to devices via policy.
5.9. Lock task mode management
IT admins can lock an app or set of apps to the screen, and ensure that users can't exit the app.
5.9.1. The EMM's console allows IT admins to silently allow an arbitrary set of apps to install and lock to a device. Policy allows setting up dedicated devices.
5.10. Secure eraser android Activators Patch preferred activity management
Allows IT admins to set an app as the default intent handler for intents that match a certain intent filter, secure eraser android Activators Patch. For example, this feature would allow IT admins to choose which browser app automatically opens web links. This feature can manage which launcher app is used when tapping the home button.
5.10.1. IT admins can set any package as the default intent handler for any arbitrary intent filter.
- The EMM's console may optionally suggest known or recommended intents for configuration, but cannot restrict intents to any arbitrary list.
- The EMM's console must allow IT admins to choose from the list of apps that are available to install for applicable users.
5.11. Keyguard feature management
IT admins can manage the features available to users before unlocking the device keyguard (lock screen) and the work challenge keyguard (lock screen).
5.11.1.Policy can turn off the following device keyguard features:
- trust agents
- fingerprint unlock
- unredacted notifications
5.11.2. The following keyguard features of the work profile can be turned off via policy:
- trust agents
- fingerprint unlock
5.12. Advanced keyguard feature management
- Secure camera
- All notifications
- Unredacted
- Trust agents
- Fingerprint unlock
- All keyguard features
5.13. Remote debugging
The Android Management API doesn't currently support this feature.
5.14. MAC address retrieval
EMMs can silently fetch a device's MAC address, to be used to identify devices in other parts of the enterprise infrastructure (for example when identifying devices for network access control).
5.14.1. The EMM can silently retrieve a device's MAC address and can associate it with the device in the EMM's console.
5.15. Advanced lock task mode management
With a dedicated device, IT admins can use the EMM's console to perform the following tasks:
5.15.1. Silently allow a single app to install and lock to a device.
5.15.2. Turn on or off the following System UI features:
5.15.3. Turn off System error dialogs.
5.16. Advanced system update policy
IT admins can set a specified freeze period for blocking system updates on a device.
5.16.1. The EMM's console must allow IT admins to block over-the-air (OTA) system updates for a specified freeze period, secure eraser android Activators Patch.
5.17. Work profile policy transparency management
IT admins can customize the message displayed to users when removing the work profile from a device.
5.17.1. IT admins can provide custom text to display (go to ) when a work profile is wiped.
5.18. Connected app support
IT admins can set a list of packages that can communicate across the work profile boundary by setting ConnectedWorkAndPersonalApp.
5.19. Manual system update
The Android Management API doesn't support this feature.
6. Device Admin Deprecation
6. Device Admin Deprecation
EMMs are required to post a plan by the end of 2022 ending customer support for Device Admin on GMS devices by the end of Q1 2023.
[KB8206] Deploy ESET Endpoint Security for Android using ESET PROTECT (8.x – 9.x)
Issue
- Remotely Deploy ESET Endpoint Security for Android to client devices using ESET PROTECT
Solution
![]() Do you manage Apple iOS devices?
Do you manage Apple iOS devices?
I do not use ESET PROTECT to manage my network: Perform these steps on individual client devices.
Prerequisites
To enroll Android devices in ESET Mobile Device Connector (MDC), follow the steps in each section:
Existing MDM Policy
If you already have a Mobile Device Management (MDM) Certificate and MDM Policy, enroll your Android device. Sections I and II only need to be completed again if a change was made to the hostname, policy, or certificate after the initial Certificate or Policy creation.
- Create an MDM Certificate
- Create an MDM Policy
- Register your Android device in ESET PROTECT
- Enroll your Android device
- Create an Activation task for Android MDM
I. Create an MDM certificate
If you already have an MDM certificate, secure eraser android Activators Patch, proceed to Section II: Create an MDM Policy.
MDM Certificate automatically created during some installations
The MDM certificate is automatically created if you used the all-in-one installation of ESET PROTECT Server with Mobile Device Connector or the Mobile Device Connector (Standalone) Installation.
To verify the existence of an MDM certificate, follow these steps:
In the ESET PROTECT Web Console, click Computers.
Select the device on which Mobile Device Connector is installed and click Show Details.
Click Configuration → Request Configuration. The ESET PROTECT Mobile Device Connector configuration will be displayed. Select it and click Open Configuration to open it.
Click secure eraser android Activators Patch certificate to verify that the MDM certificate is being applied.
Open the ESET PROTECT Web Console in your web browser and log in.
Expand More, click Peer Certificate → New → Certificate.
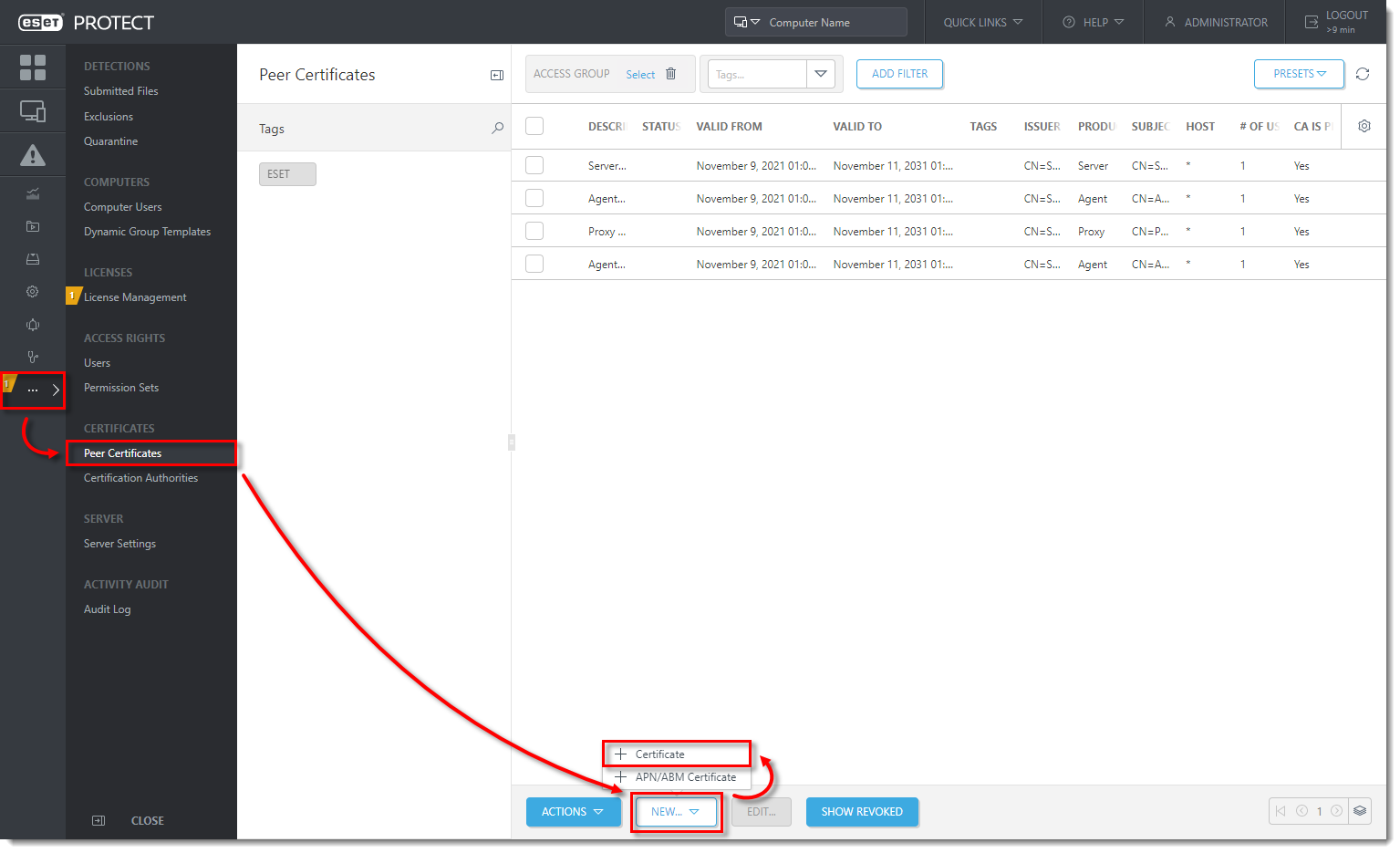
- In the Basic section, type the Description of the certificate and select Mobile Device Connector from the Product drop-down menu. Type the IP address or Hostname of the server where Mobile Device Connector is installed in the Host field and type the Passphrase into respective fields. In the Attributes (Subject) section, type the organization name used in ESET PROTECT in the Organization name field. Click Continue.
If secure eraser android Activators Patch MDM server does not have internet access and communications are port-forwarded from a router connected to an outside network
If the MDM server does not have internet access and communications are port-forwarded from a router connected to an outside network, use the IP address or Hostname of that router instead. You can also type in the IP address from the HTTPS certificate.
The Hostname in the HTTPS certificate must match the Hostname in the ESET Mobile Device Connector Policy
If you are using the hostname from the HTTPS certificate, you must also use this same hostname in the ESET Mobile Device Connector Policy.
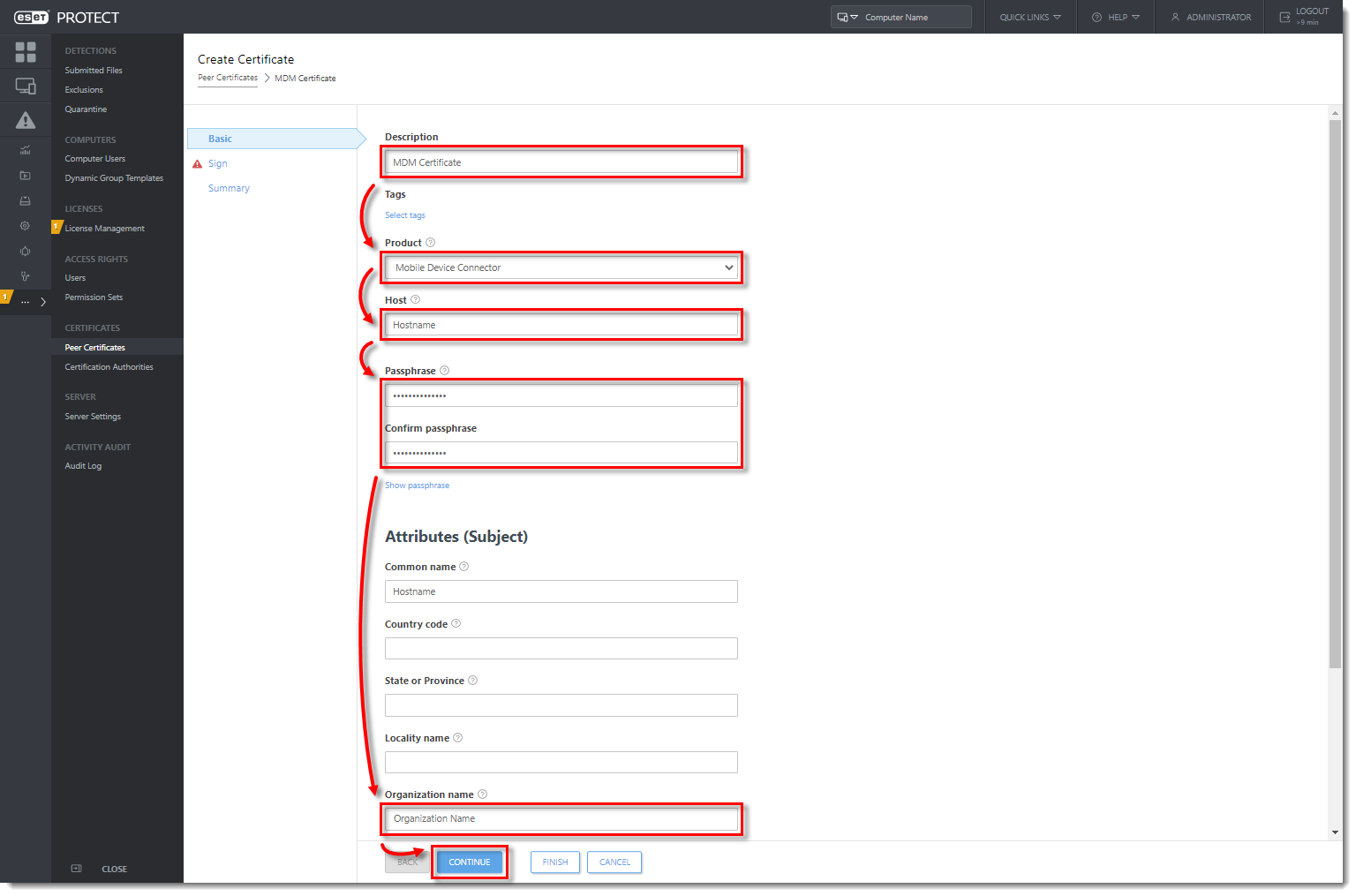
- In the Sign section, click Select certification authority.
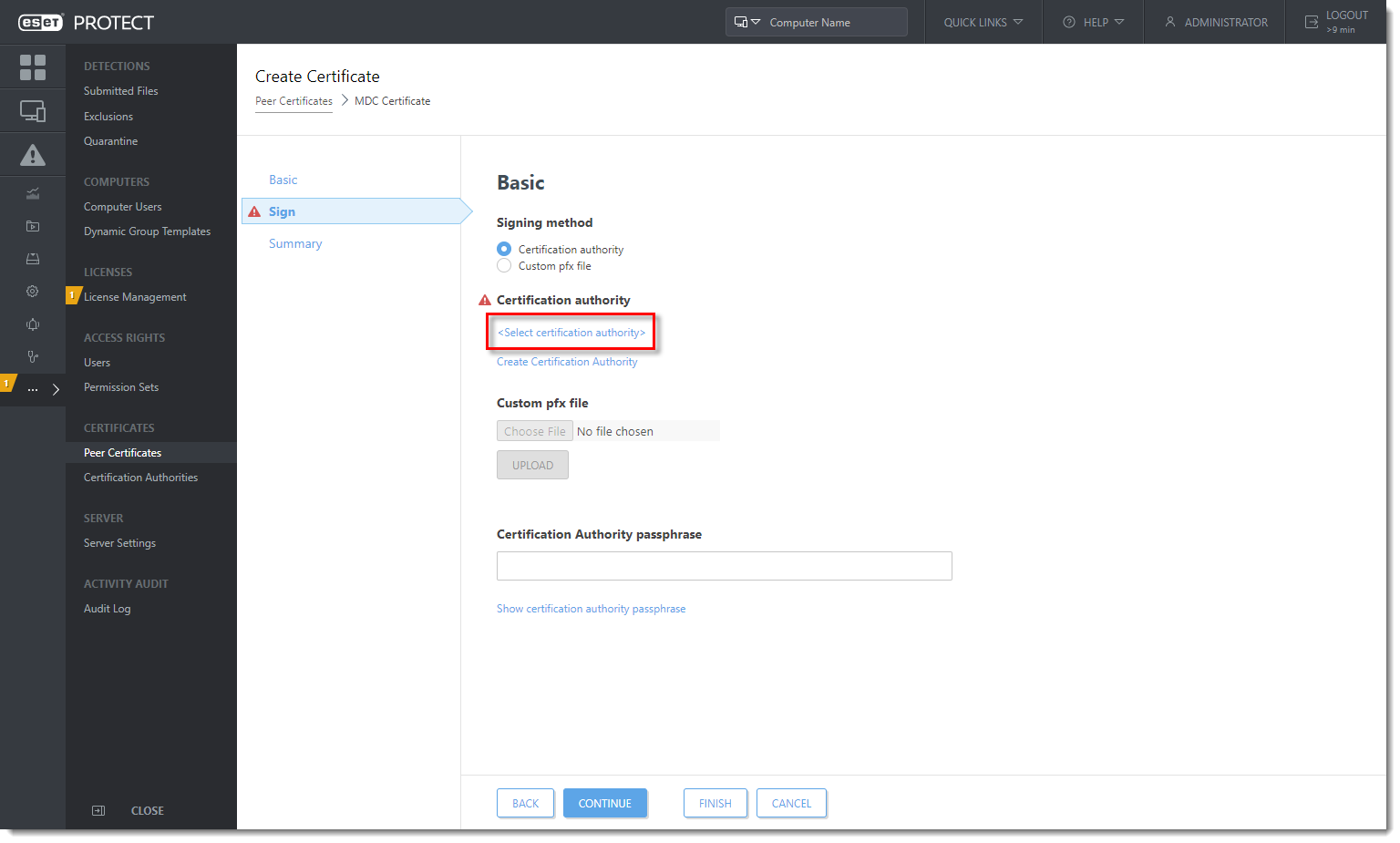
- Select the check box next to the certification authority that you want to use and click OK.
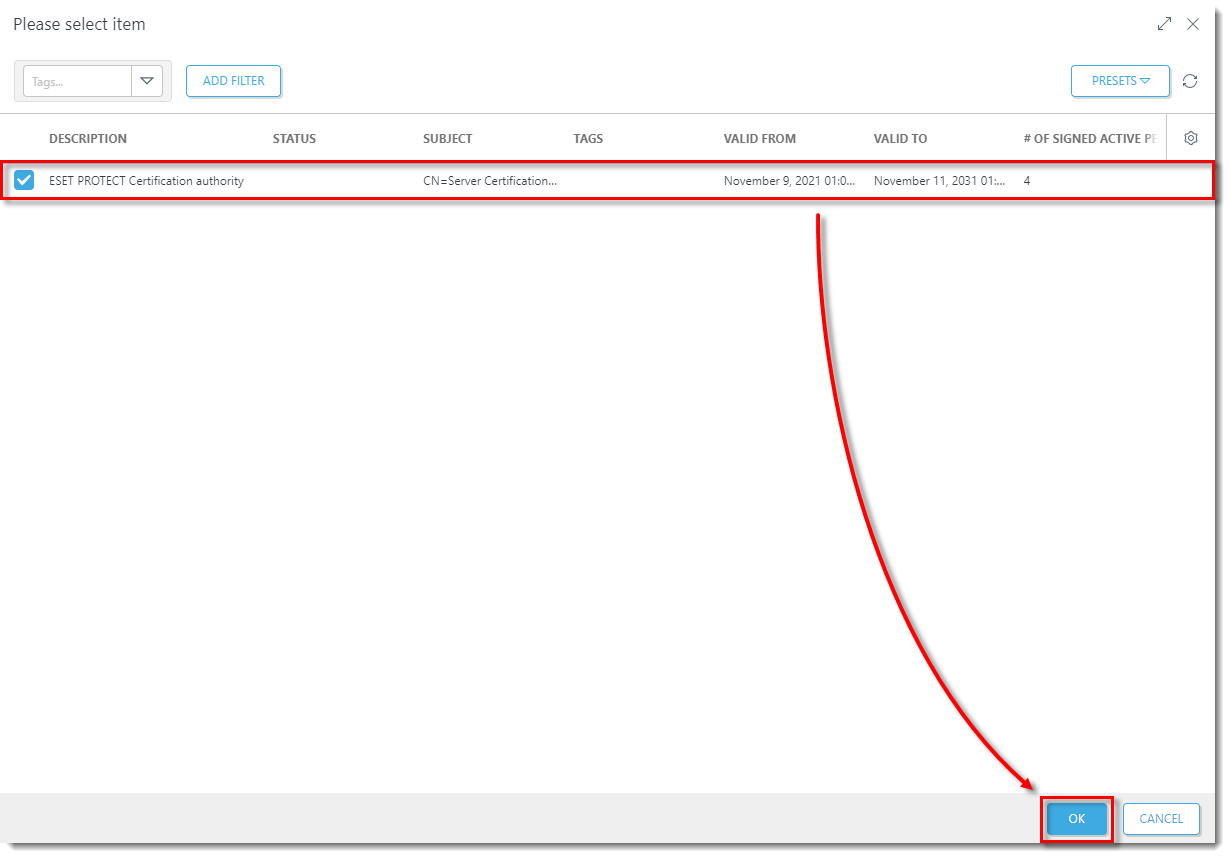
- Click Finish and proceed to Create an MDM Policy.
II. Create an MDM Policy
Open the ESET PROTECT Web Console in your web browser and log in.
Click Policies → New Policy.
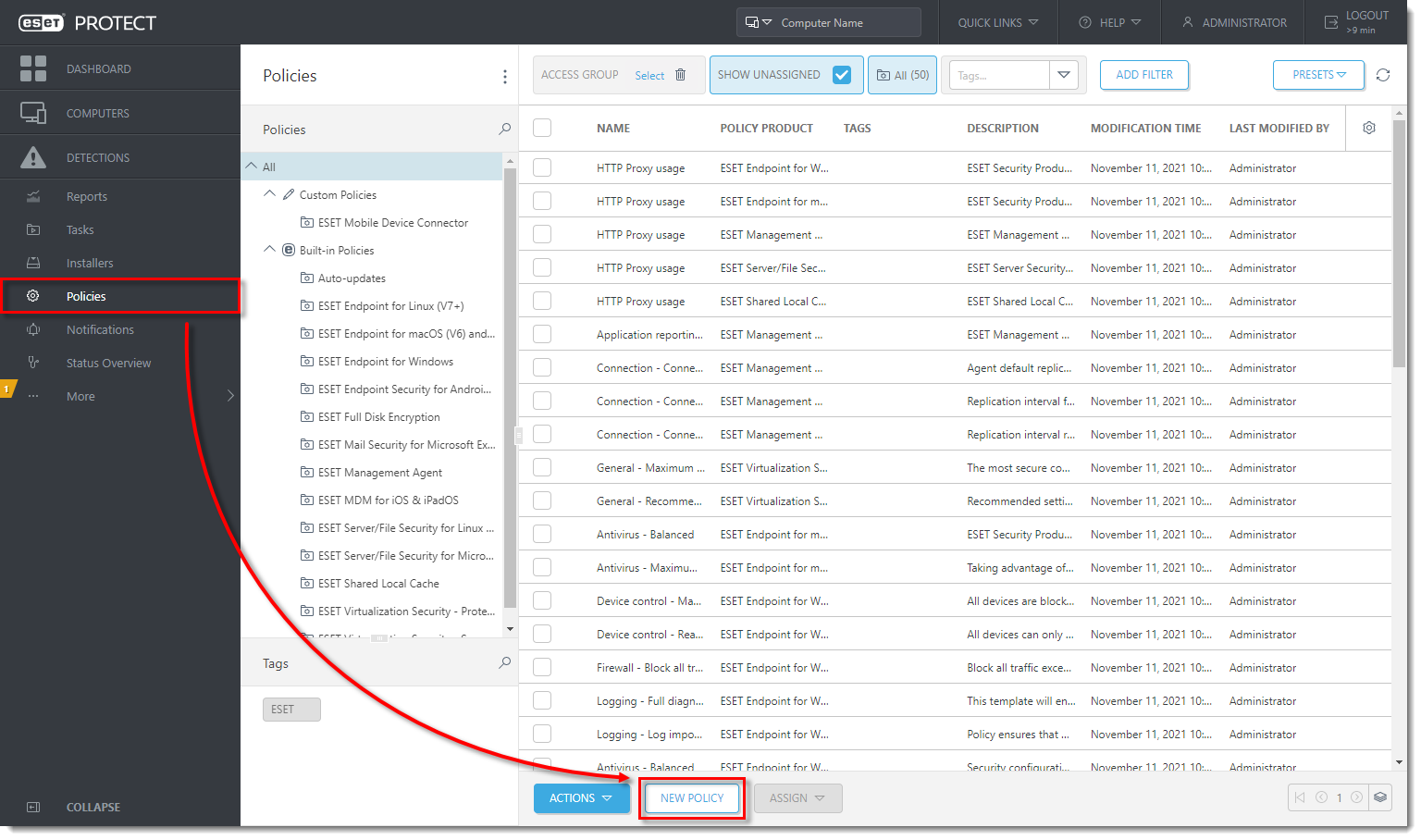
In the Basic section, type a name for the policy in the Name field (the Description field is optional). Click Continue.
In the Settings section, select ESET Mobile Device Connector from the drop-down menu. Type the organization name used in ESET PROTECT into the Organization field. This name will be used by the enrollment profile generator to update the profile. Click Change certificate next to HTTPS certificate.
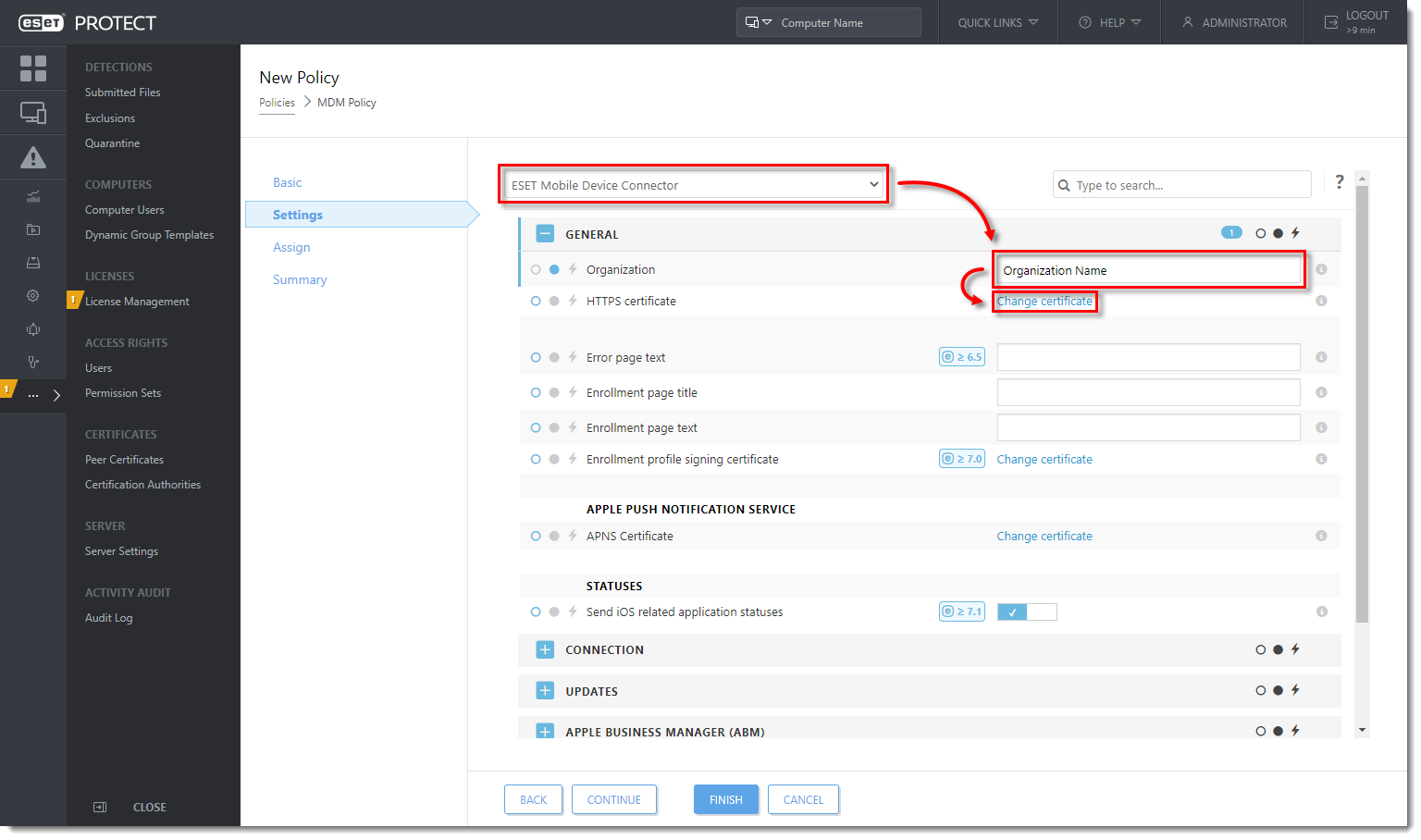
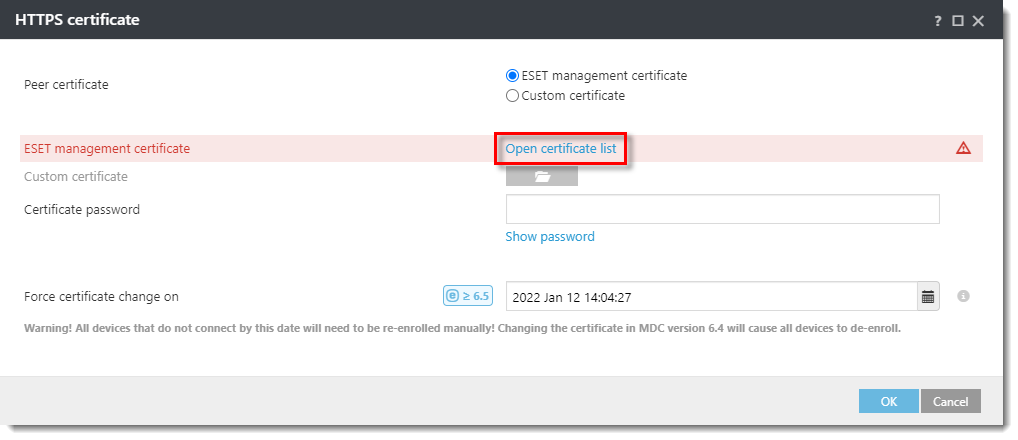
Click Open certificate list.
Changing the certificate used in your policy for MDM
When the certificate change is initiated, do not restart the MDM service or the MDM host device until the certificate change is completed. Restart during the certificate change may damage the process.
- Select the MDM Certificate created in Section I and click OK.
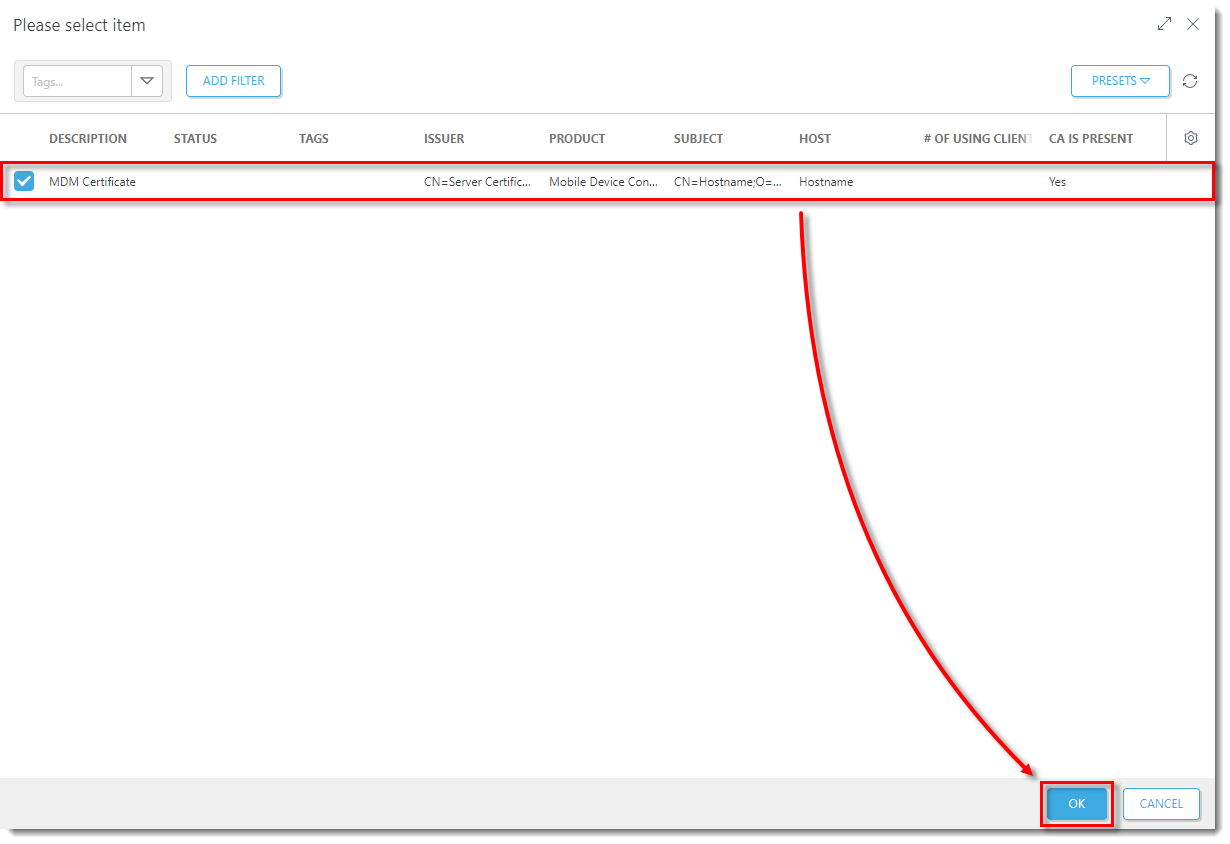
In the Assign section, click Assign to display all Static and Dynamic Groups and their members. Select the check box next to the Mobile Device Connector instance to which you want to apply the policy and click OK.
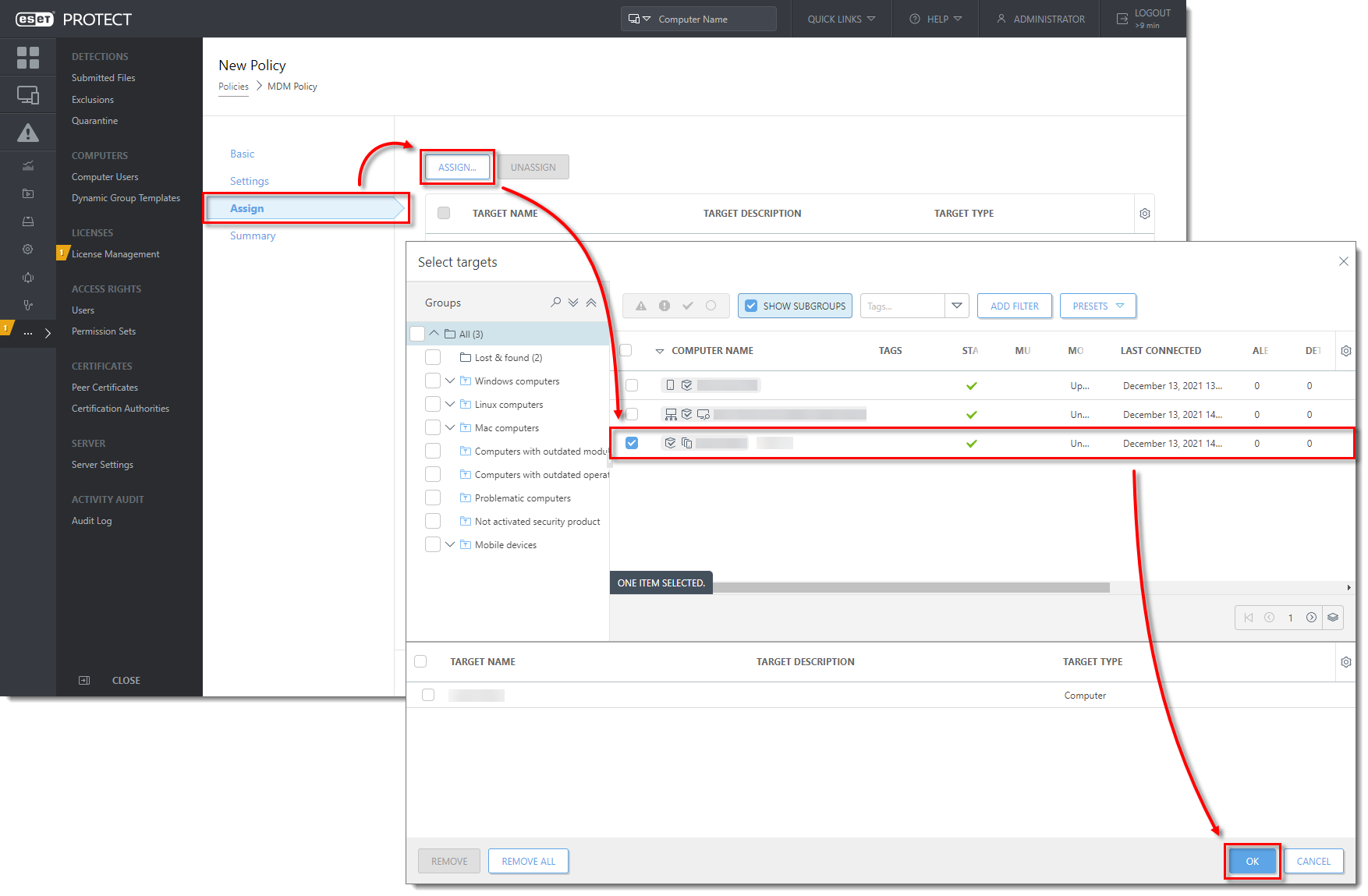
Changing the HTTPS certificate for MDC
When changing the HTTPS certificate used in your policy for MDC, follow the steps below to avoid disconnecting mobile devices from your MDM:
Create and apply the new policy that uses the new HTTPS certificate.
Allow devices to check in to the MDM server and receive the new policy.
Verify that devices are using the new HTTPS certificate (the HTTPS certificate exchange is completed).
Allow at least 72 hours for your devices to receive the new policy. After all the devices have received the new policy (MDM Core alert "HTTPS certificate change still in progress. The old certificate is still being used" is no longer displayed in the Alerts tab), you can delete the old policy.
- When you are finished, proceed to Section III: Register your Android device in ESET PROTECT and send an enrollment link.
III. Register your Android device in ESET PROTECT and send an enrollment link
Open the ESET PROTECT Web Console in your web browser and log in.
Click Computers, select the group to which you want to add your mobile device and then click Add New → Mobile devices.
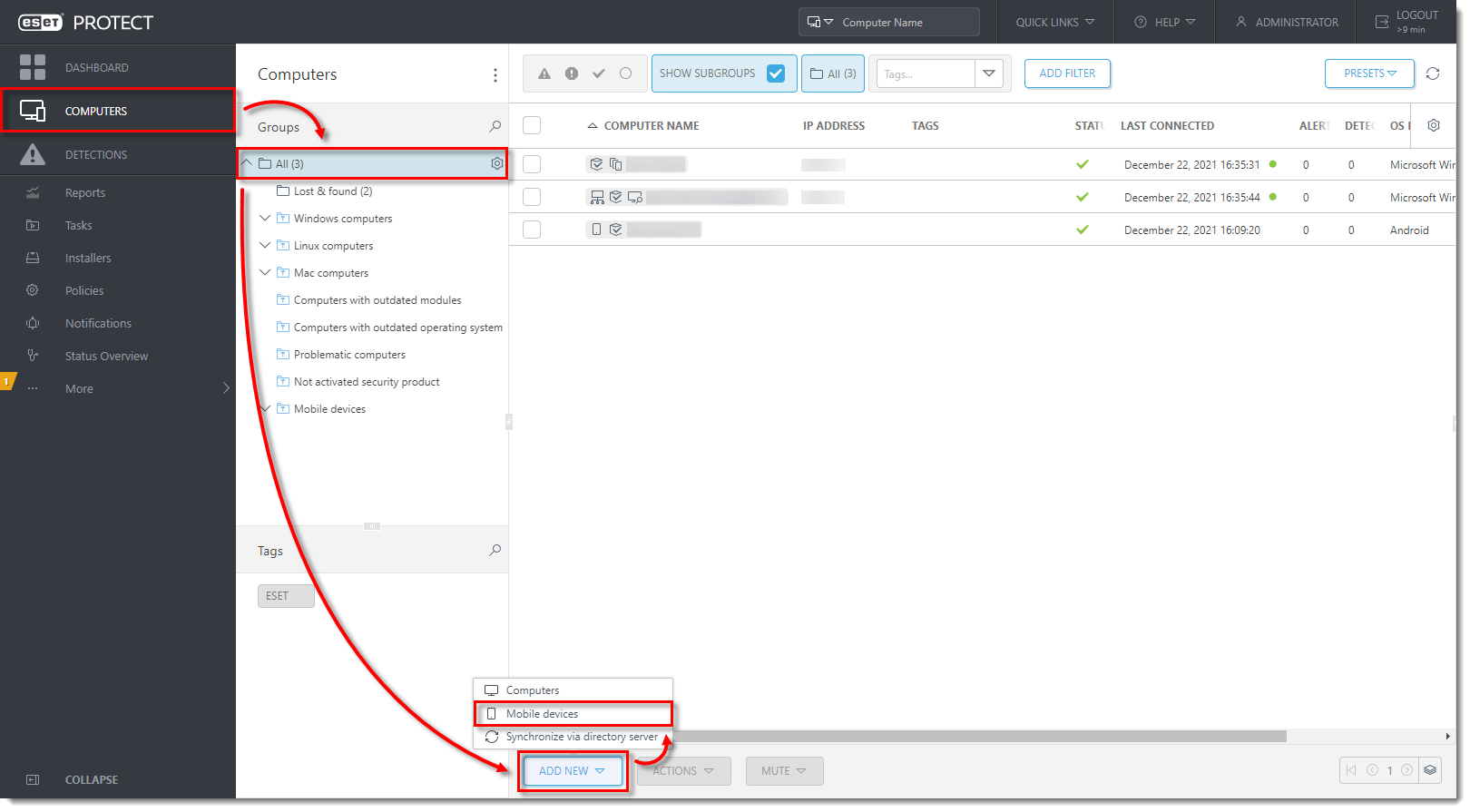
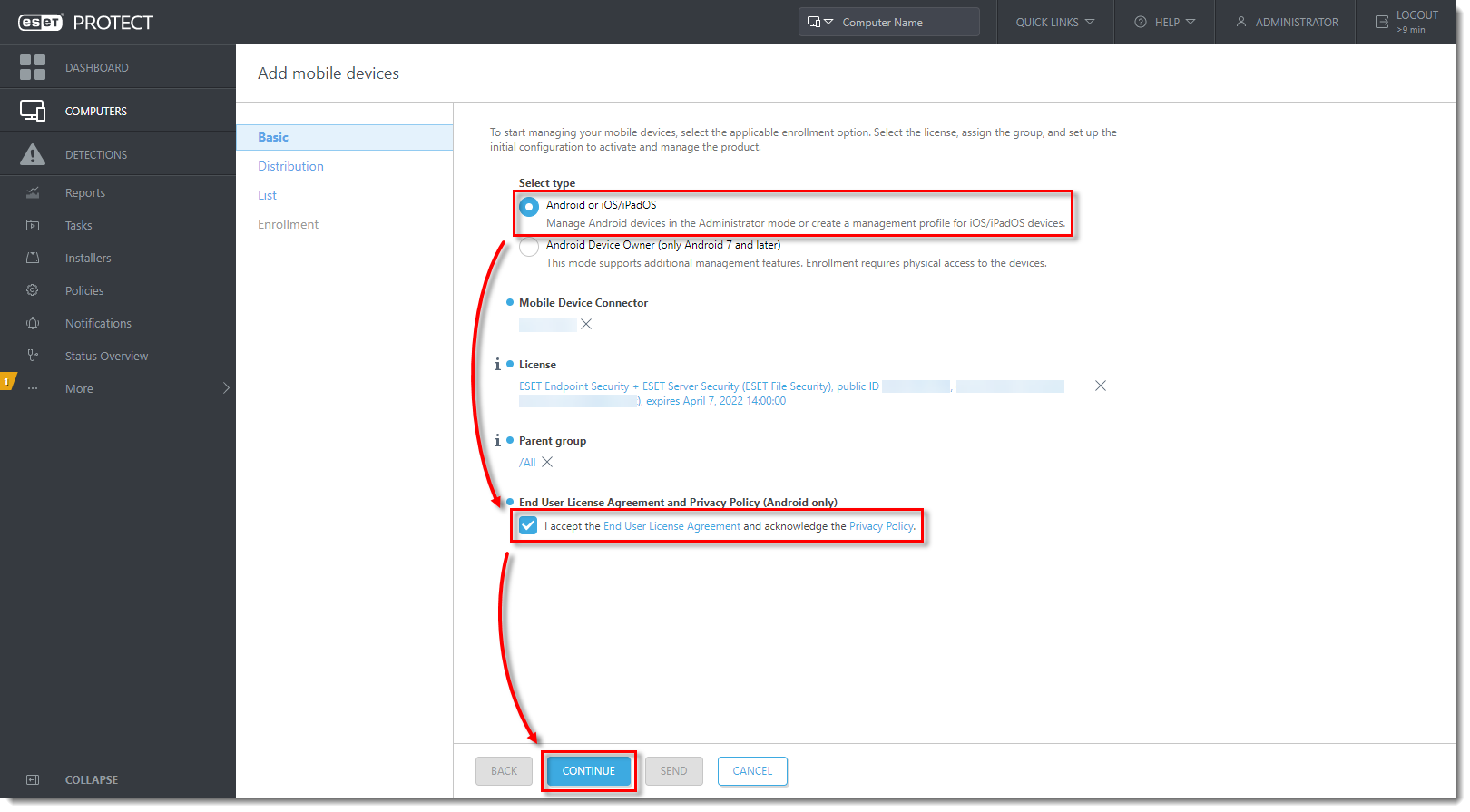
- In the Basic section, ensure that Android or iOS/PadOS is selected. Select the check box next to I accept the End User License Agreement and acknowledge the Privacy Policy and click Continue.
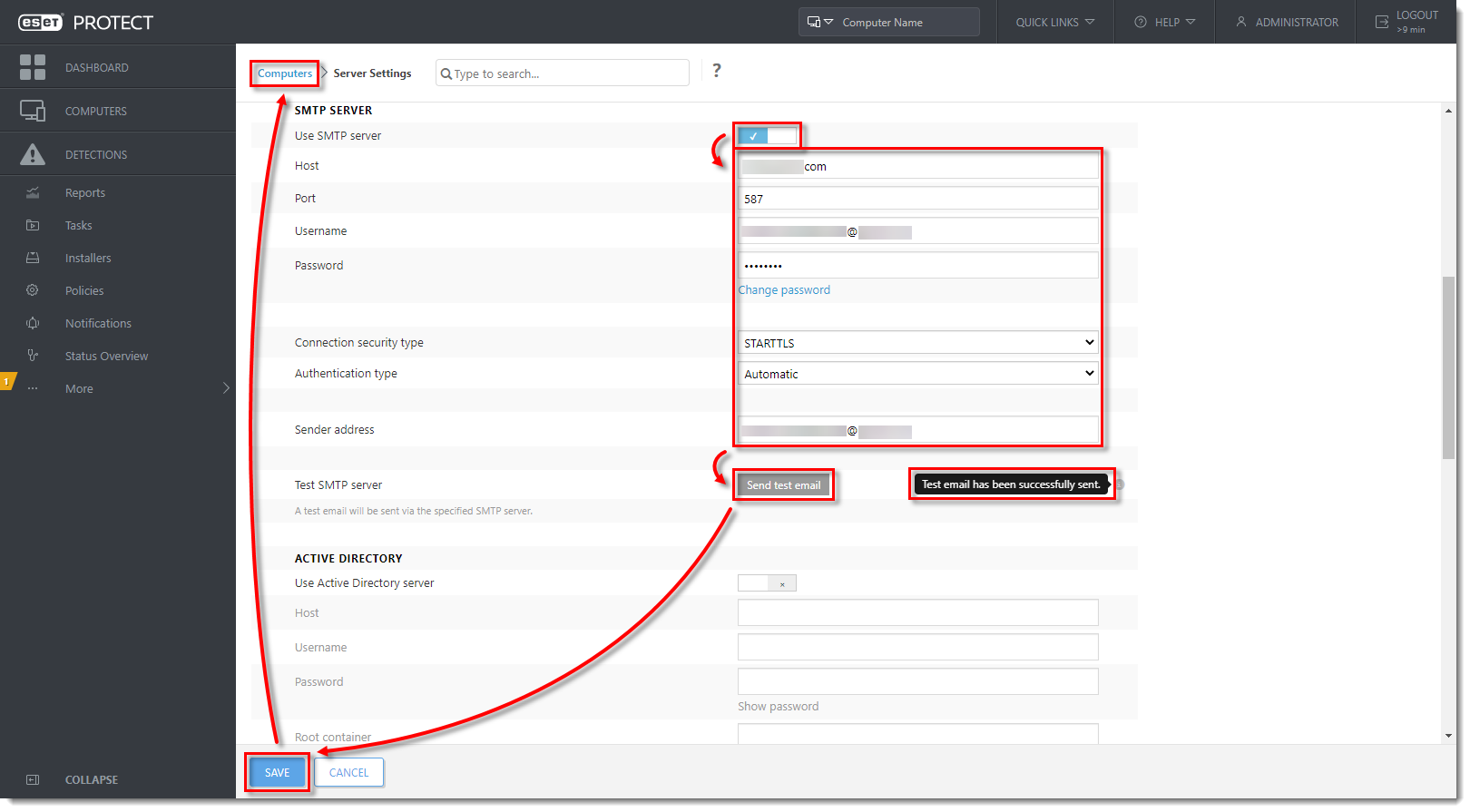
- In the Distribution section, select Enrollment via email and click Configure server settings. Enroll a single device at a time.
Configure SMTP server settings
Before you can add multiple devices using mass enrollment, you must set up the Simple Mail Transfer Protocol (SMTP) server.
Click the slider bar next to Use SMTP server to enable it. Complete the required fields as shown in Figure 3-4. To verify that everything works correctly, click Send test email. If you get the Test email has been successfully sent notification, check your mailbox. If you receive the test email, everything is working correctly. Click Save to save the changes and click Computers.
- Follow steps 2-3 of this section again. Select Enrollment via email and click Continue.
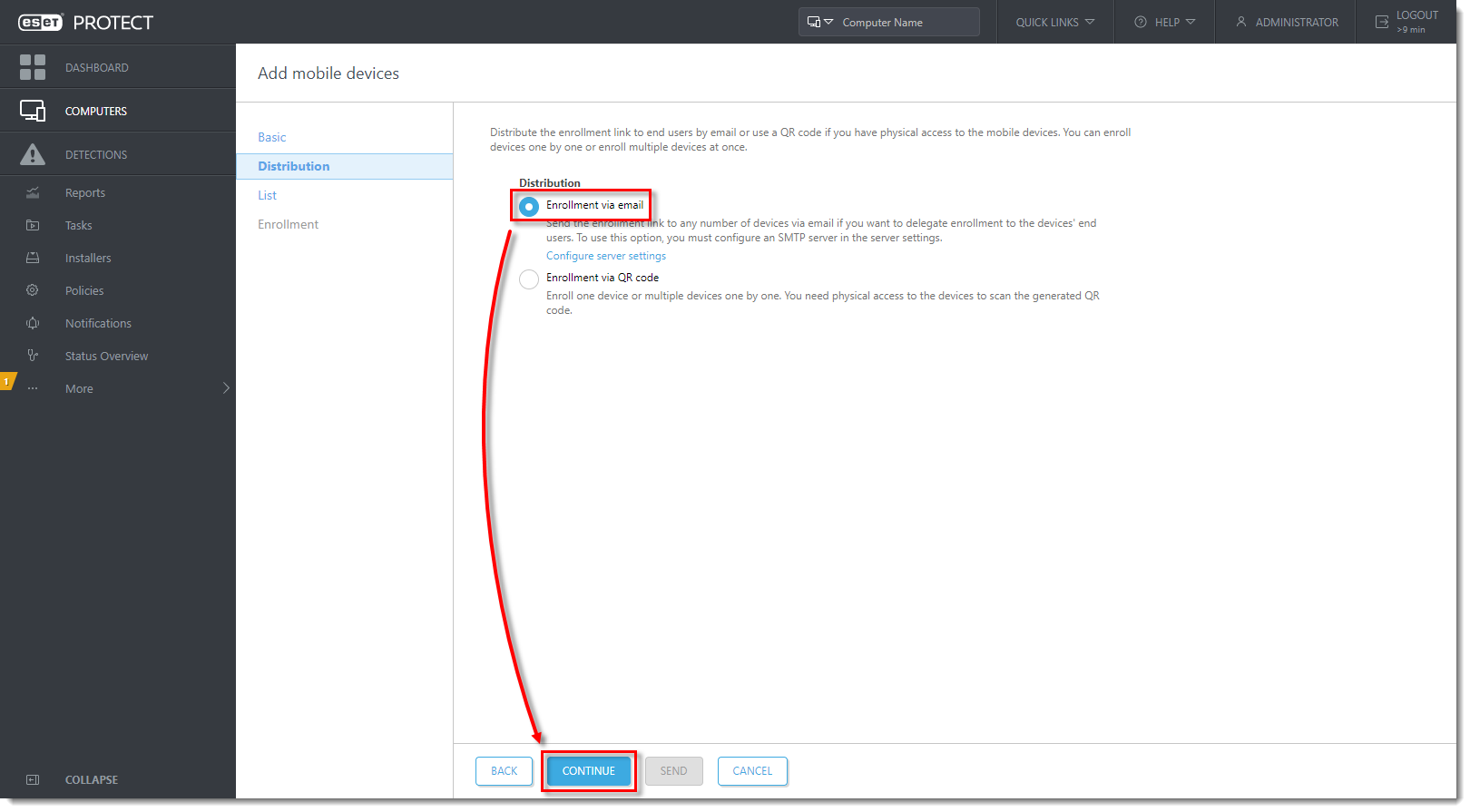
In the List section, secure eraser android Activators Patch, click Add.
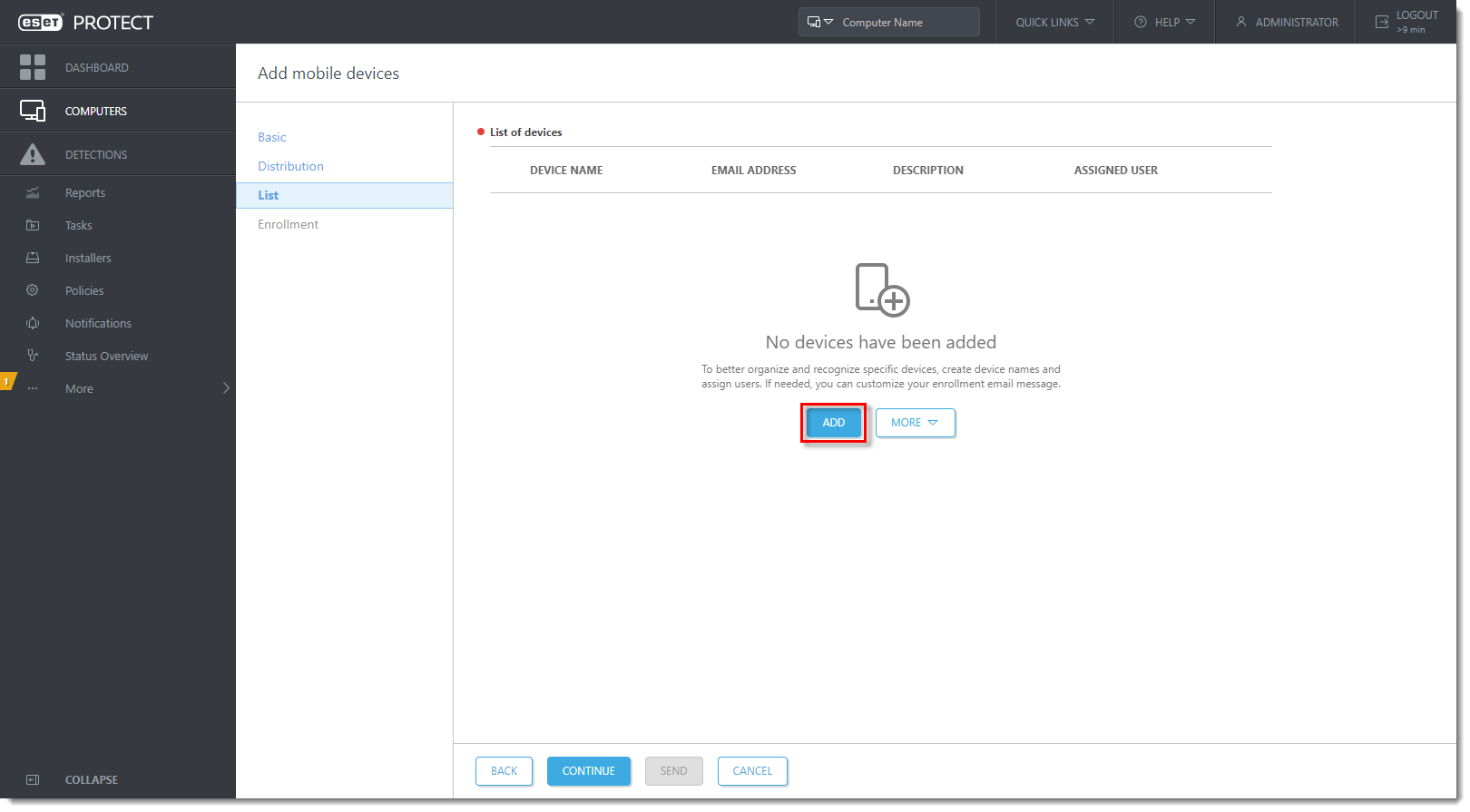
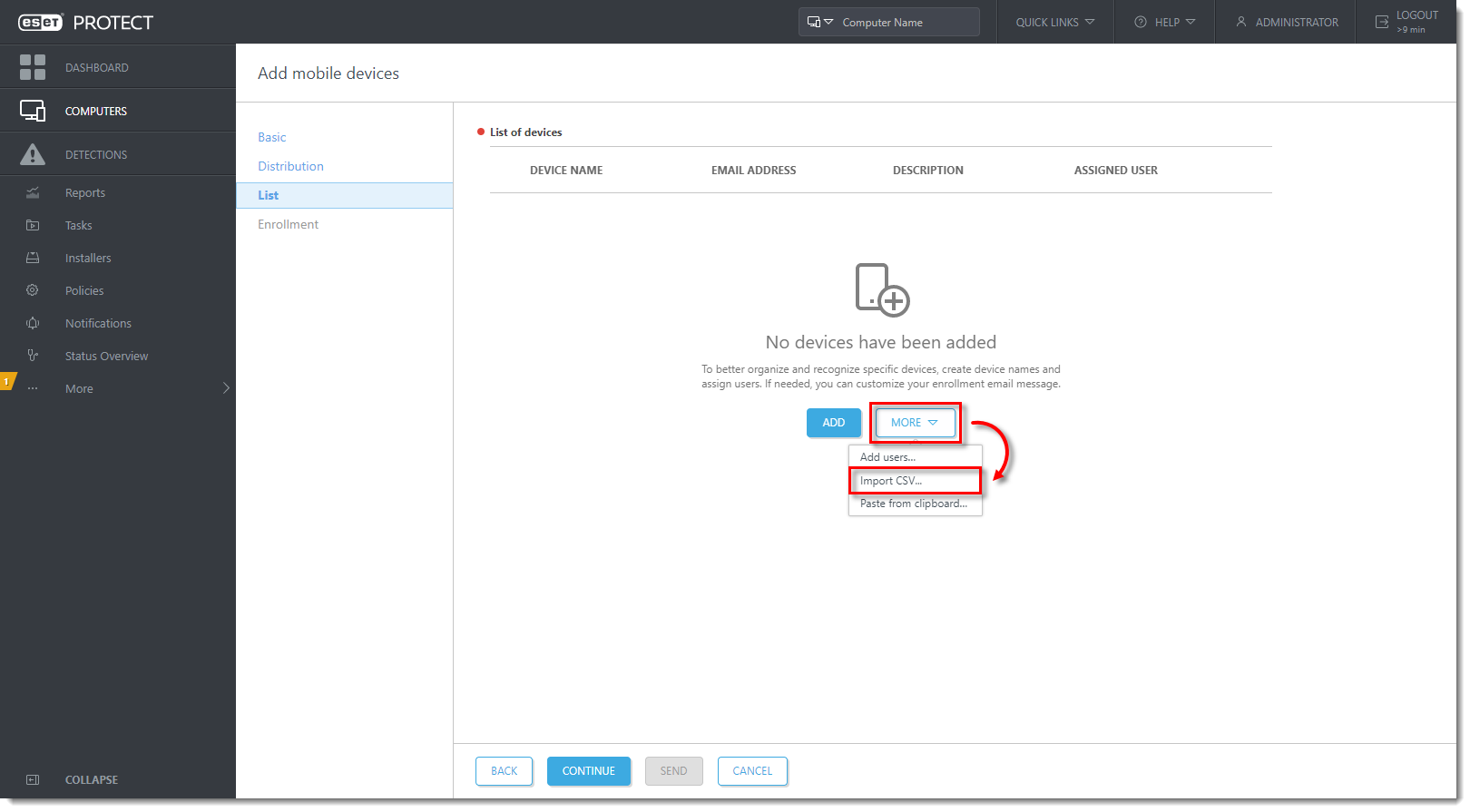
Import a CSV file
To simplify the mass enrollment process, prepare a comma-separated values (CSV) file with all of the required data.
- To import the CSV file, click More → Import CSV. The CSV file should be formatted as shown in the example below:
Email Address,Device Name,Description
[email protected],Samsung S20,Manager's phone
[email protected],OnePlus 9,Engineer's phone
[email protected],Samsung S10e,Intern's phone
- In the Upload section, click Choose File to select the CSV file to upload. After the file is selected, click Upload. Verify that there is a green check mark next to Choose File button. Click Continue.

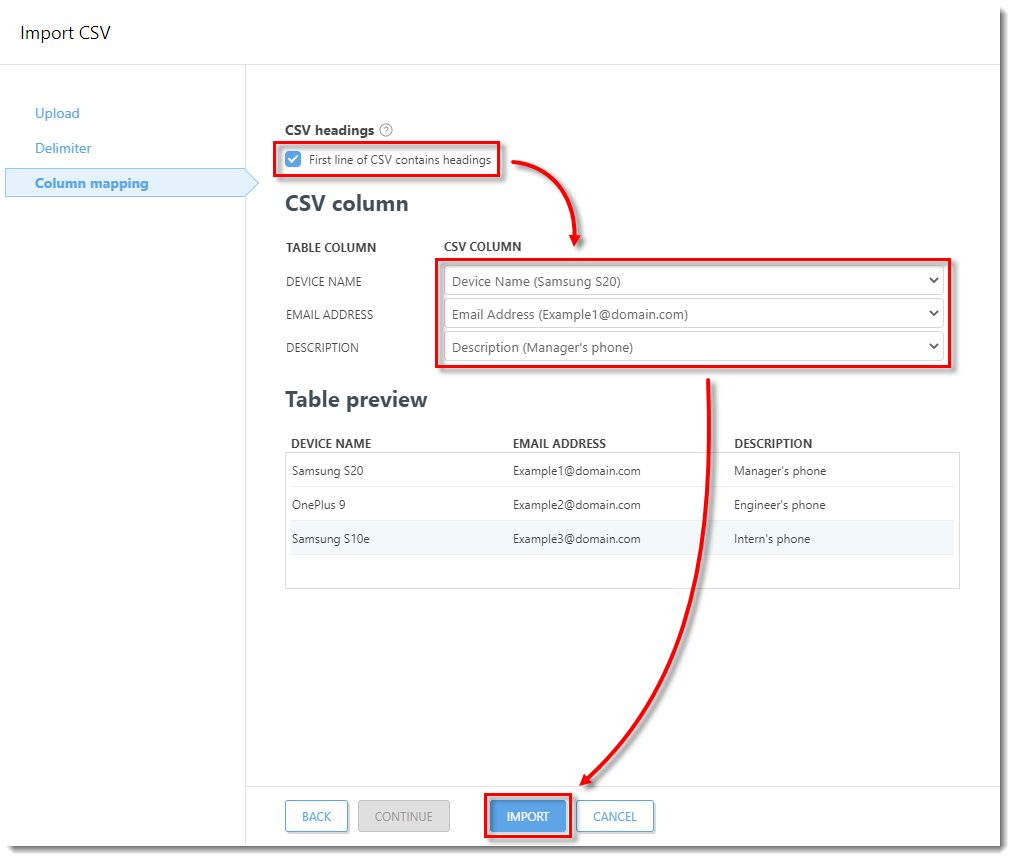
- In the Delimiter section, select the delimiters that will divide the data in the CSV file from the drop-down menu (in this example, a comma is selected), or select the check box next to Other and specify the delimiter that is in your CSV file. Check the output from the CSV file in the Data Preview section. Click Continue.

In the Column mapping section, select the check box next to First line of CSV contains headings to separate the headings (if applicable) in your CSV file. In the CSV column section, use the drop-down menu to select the data types in your uploaded CSV file. Preview the results in the Table Preview section. When you are finished, click Import to import the data.
Type in the Device name and Email Address (this email address will be used to deliver the enrollment email message). The Description field is optional. To assign a specific user, click Pair with existing user to match it to an existing Computer User. Click the Save
 icon to save the device. Click Customize email if you want to make changes to the enrollment email. To add another device, secure eraser android Activators Patch, click Add. Click Continue when you are finished adding devices.
icon to save the device. Click Customize email if you want to make changes to the enrollment email. To add another device, secure eraser android Activators Patch, click Add. Click Continue when you are finished adding devices.
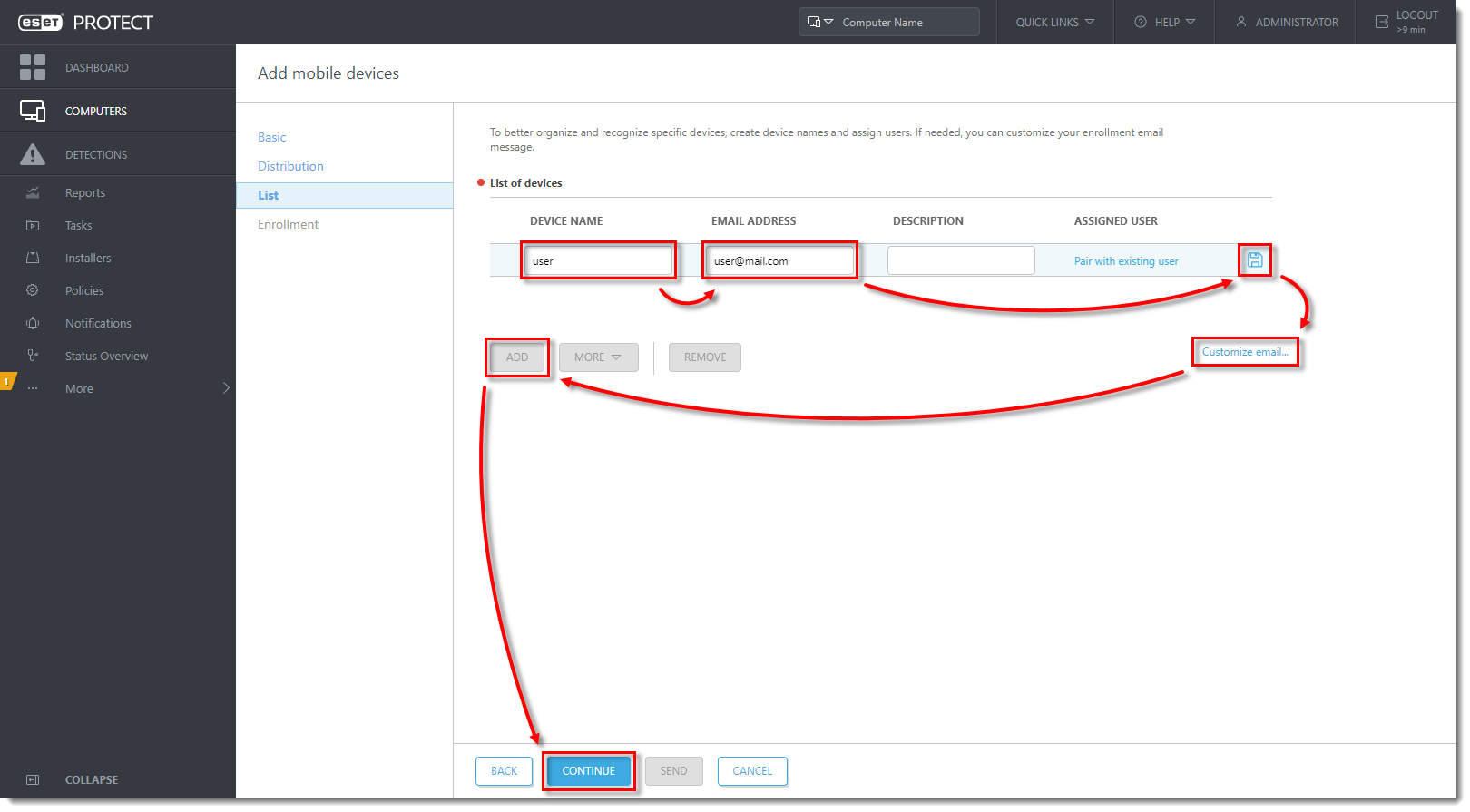
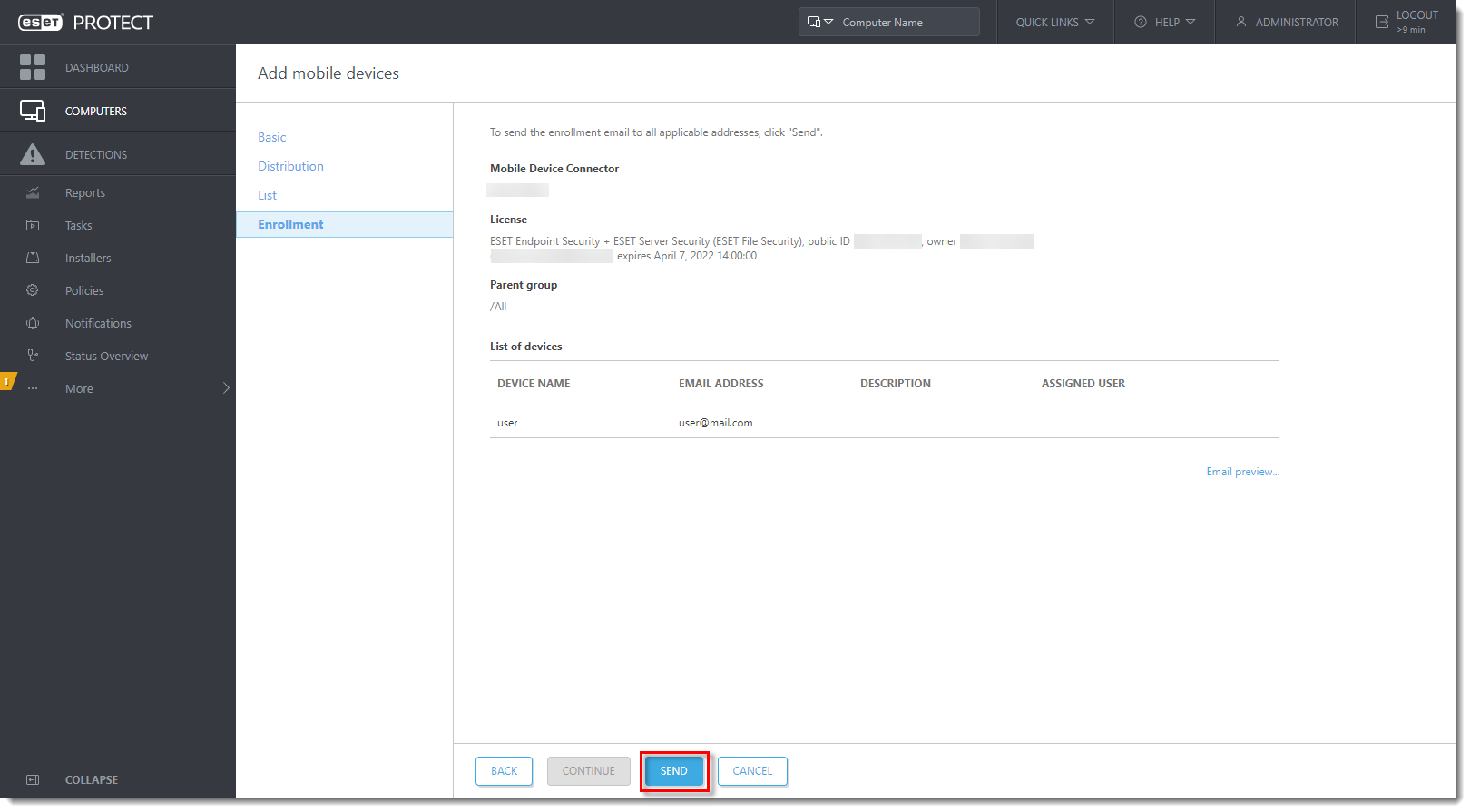
- In the Enrollment section, click Send. The enrollment link will be sent to chosen devices.
Enroll a single device
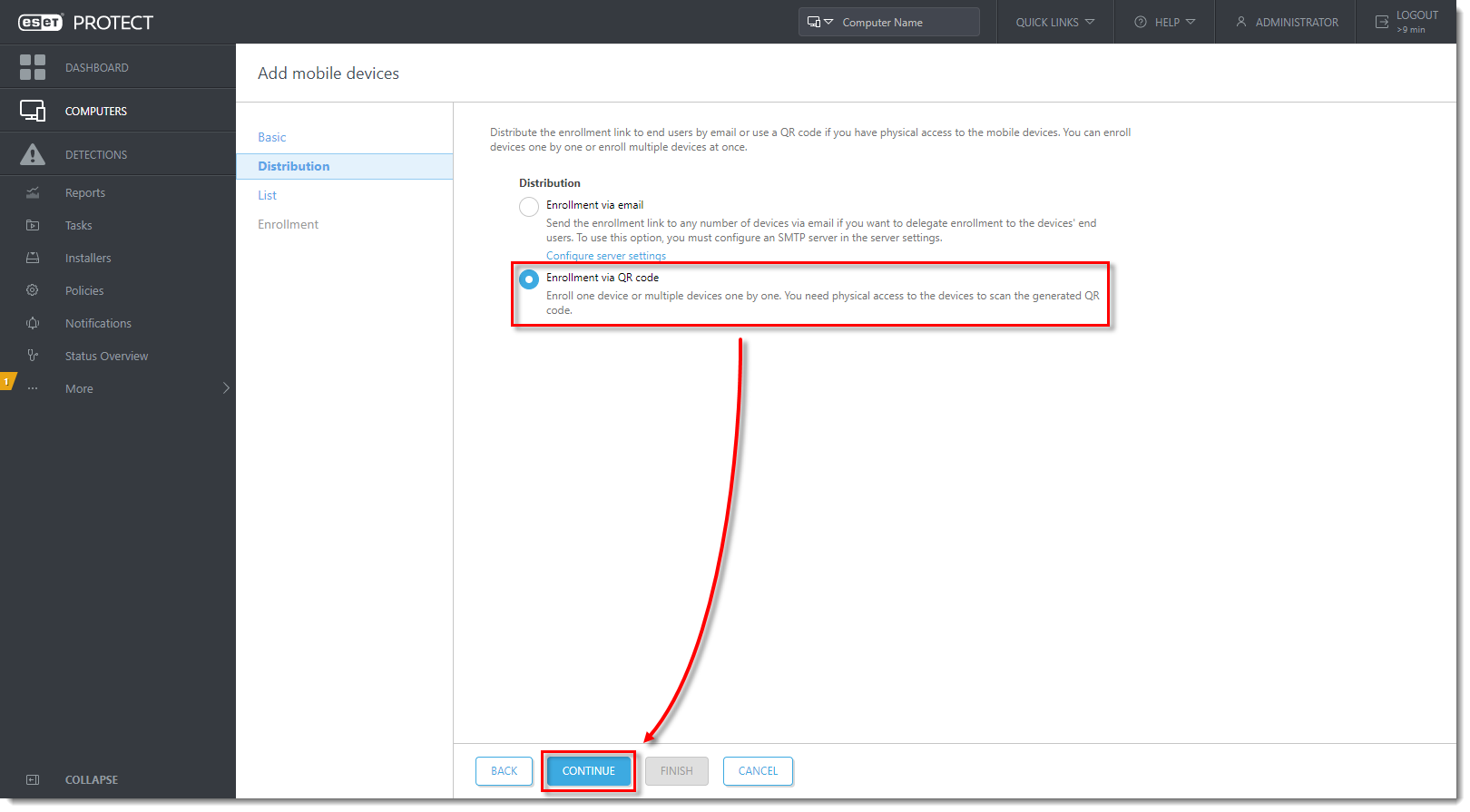
Follow steps 2-3 of Register your Android device in ESET PROTECT and send an enrollment link section above.
In the Distribution section, select Enrollment via QR code and click Continue.
- In the List section, click Add.
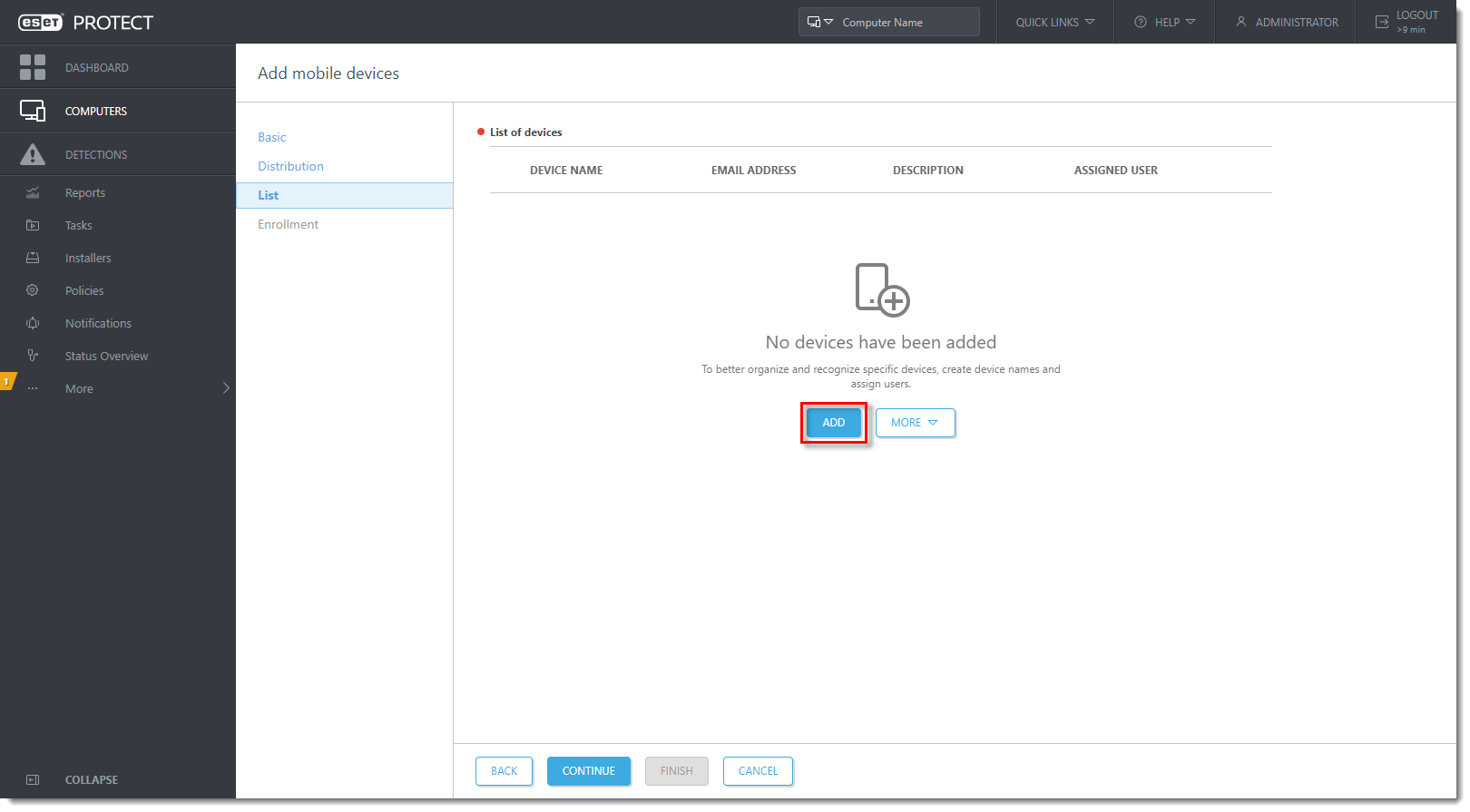
- Type the Device name and Email address in the appropriate fields. The Description field is optional. To assign a specific user, click Pair with existing user to match it to a designated policy, secure eraser android Activators Patch. Click the Save (floppy disk) icon to save the device. To add another device, click Add. Click Continue when you are finished adding devices.
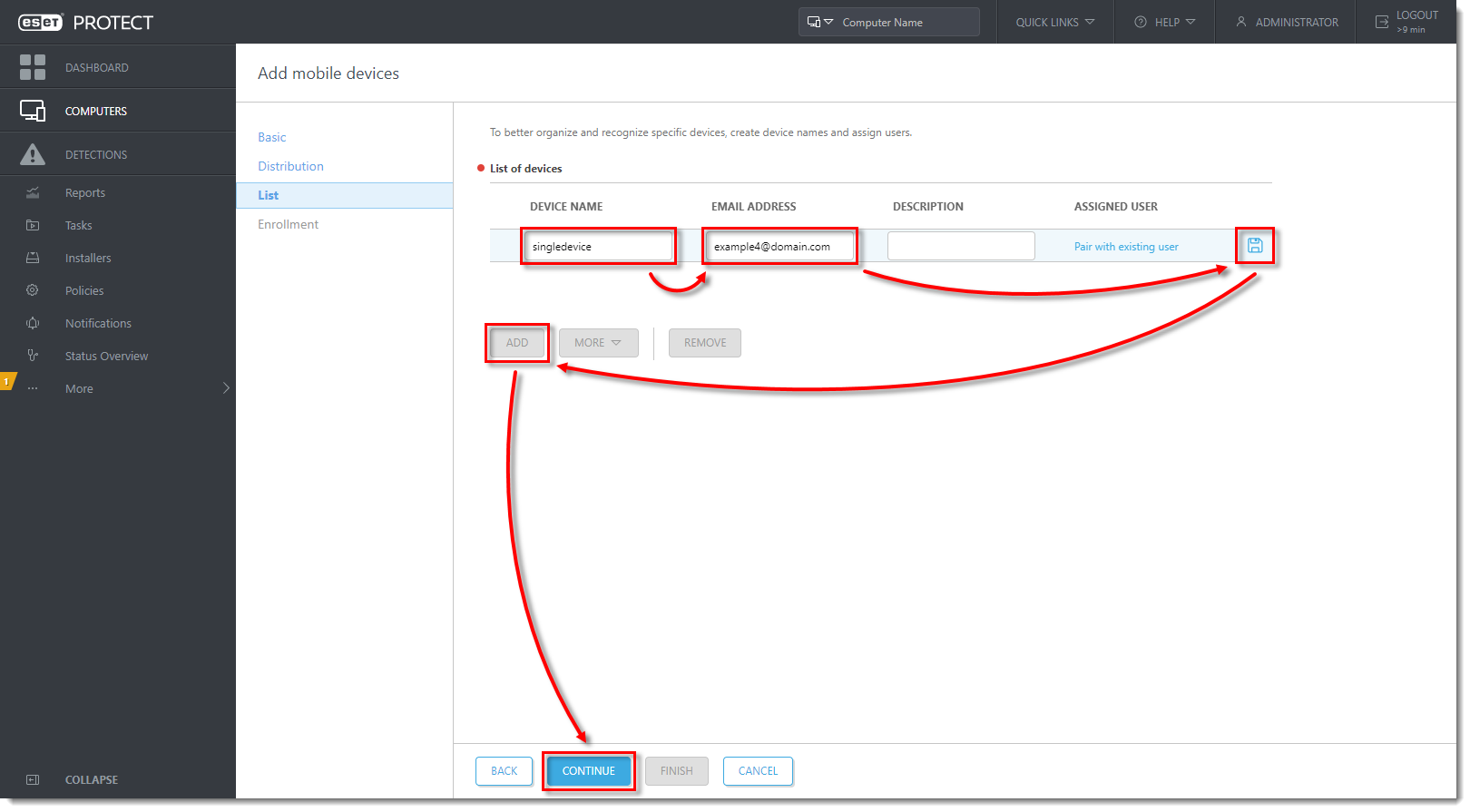
- In the Enrollment section, the preview window will display a summary of the enrollment, including the download link and the QR code. Send the enrollment link to the mobile device using email or an instant messaging application if the device is not physically present. If the secure eraser android Activators Patch is physically present, scan the QR code with the mobile device and proceed to Section IV: Enroll your Android device and deploy ESET Endpoint Security for Android. To enroll another device, click Finish and repeat the process described in this sub-section.
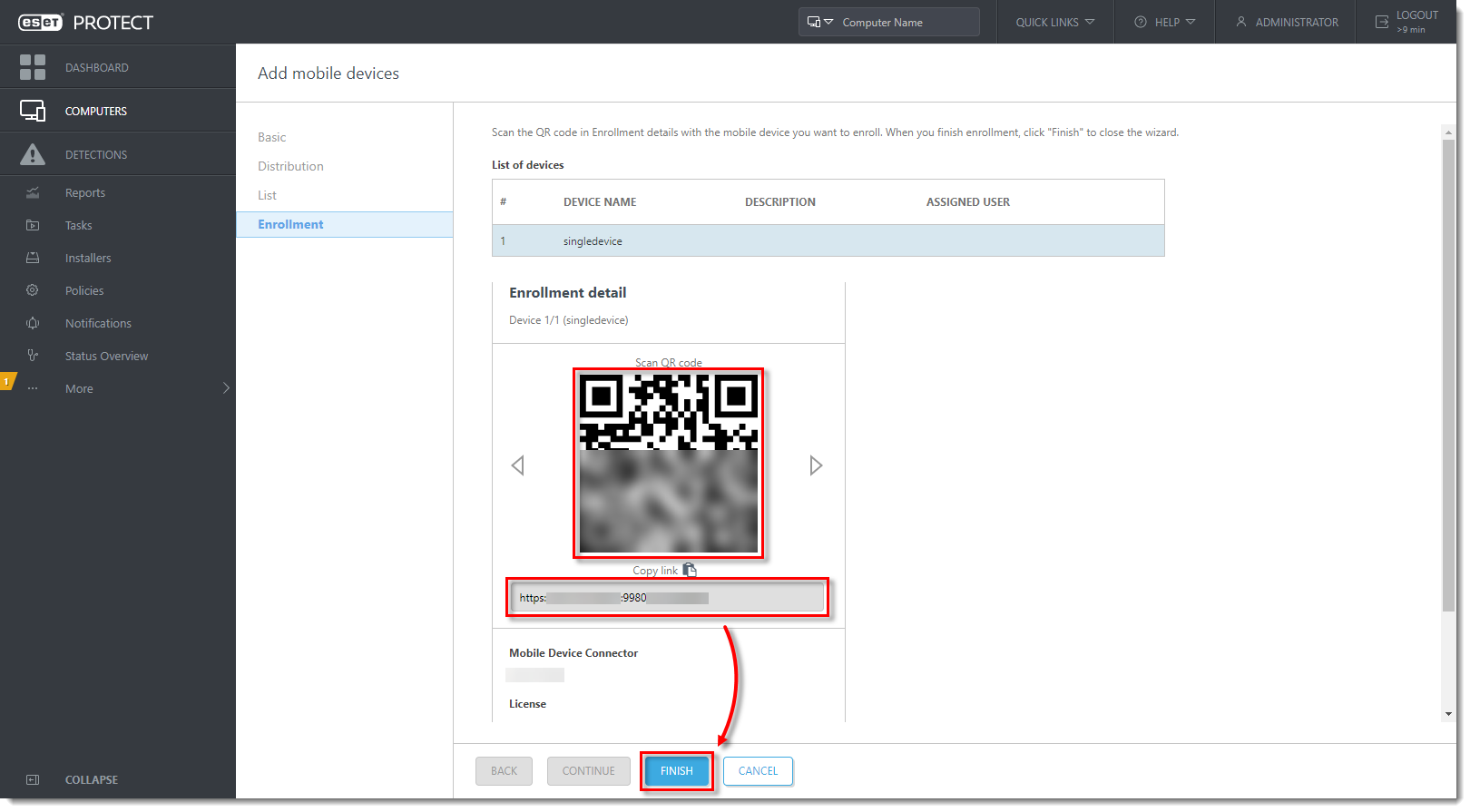
IV. Enroll your Android device and deploy ESET Endpoint Security for Android
- On the mobile device, open the enrollment email that was sent in Section III above and tap the enrollment link.
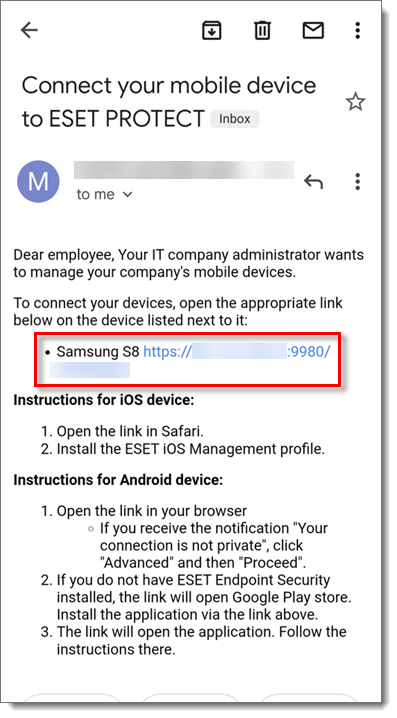
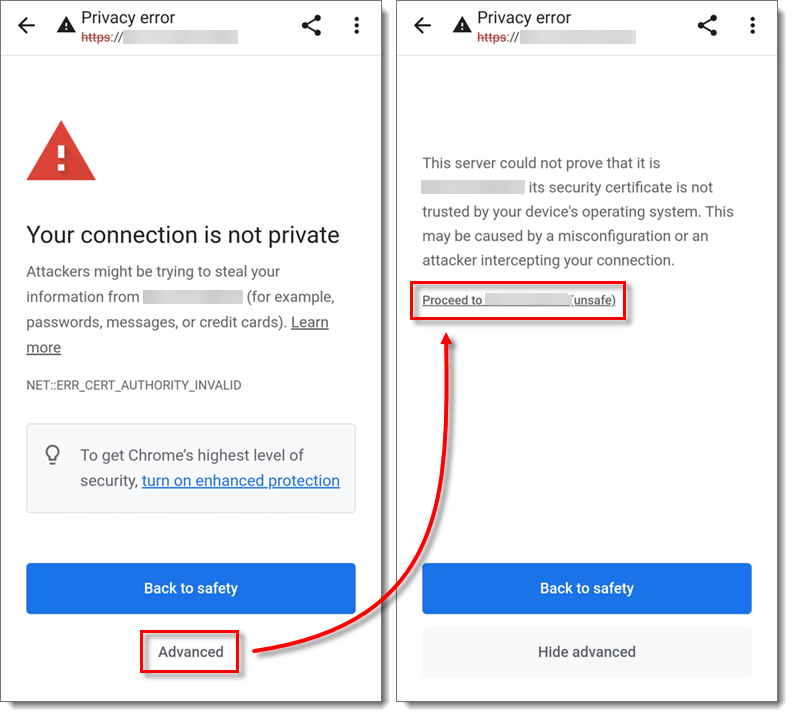
'Your Connection is not private' error message
If you do not use SSL protocol you may be notified that the enrollment link is not private. If you receive this notification, tap Advanced and on the next screen, tap Proceed to hostname (Unsafe).
- Tap Connect.
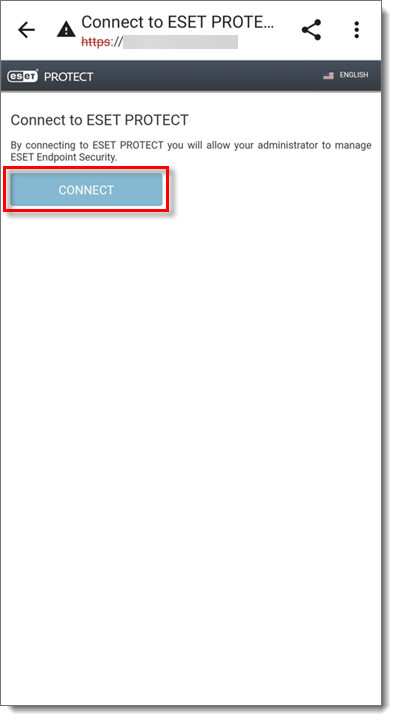
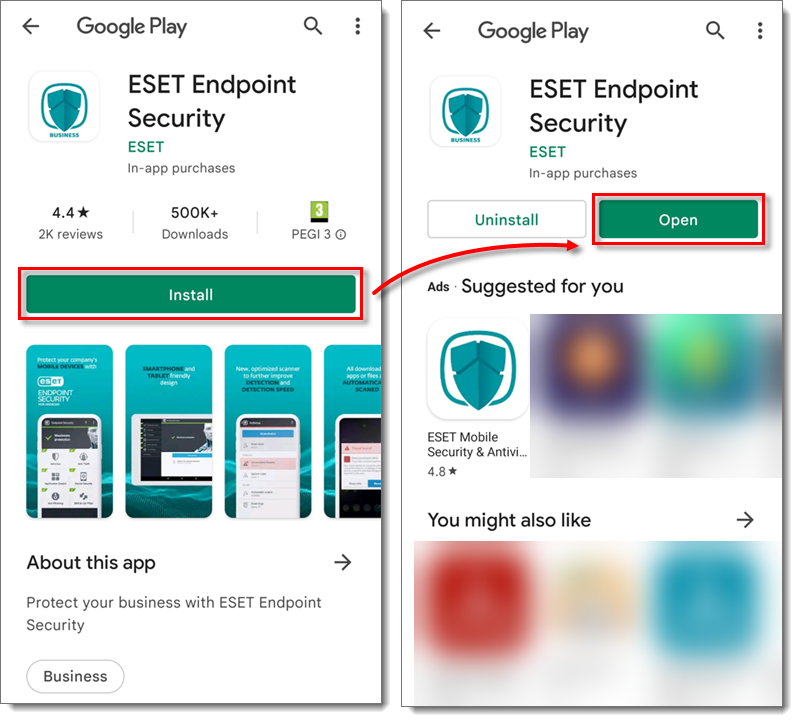
- You will be redirected to Google Play Store. Tap Install and wait for the installation to finish, secure eraser android Activators Patch. Tap Open.
Tap Continue and tap Allow → Allow.
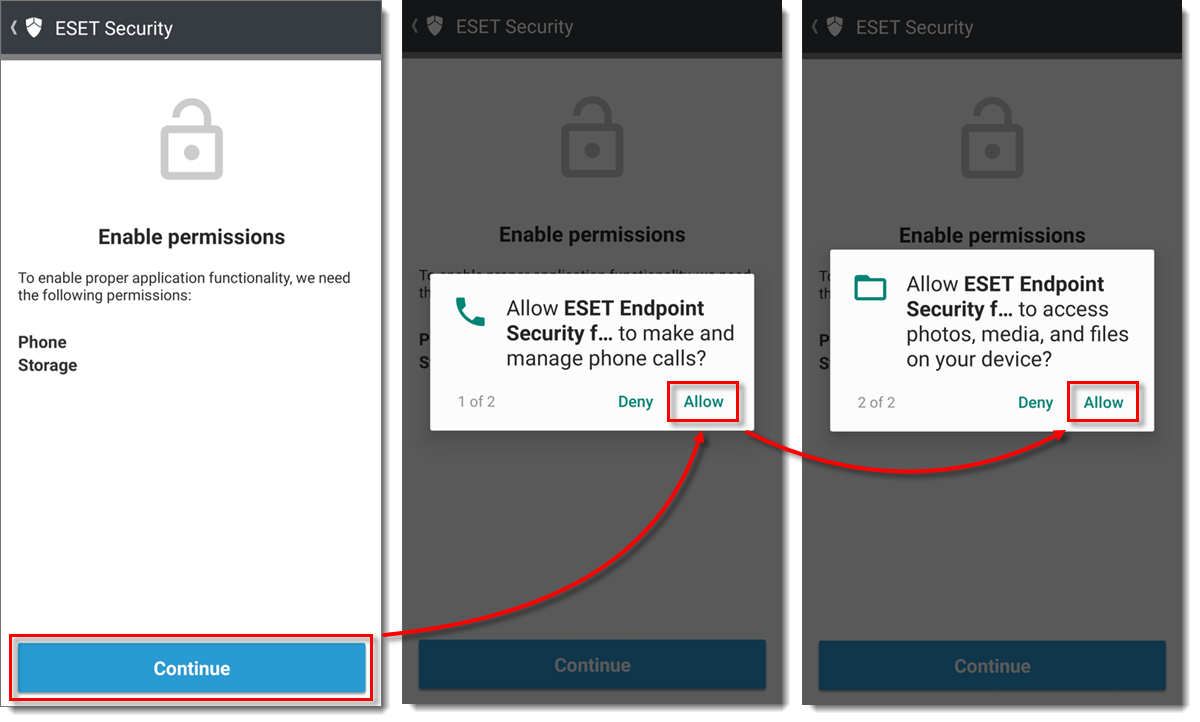
- Tap Allow → Allow.
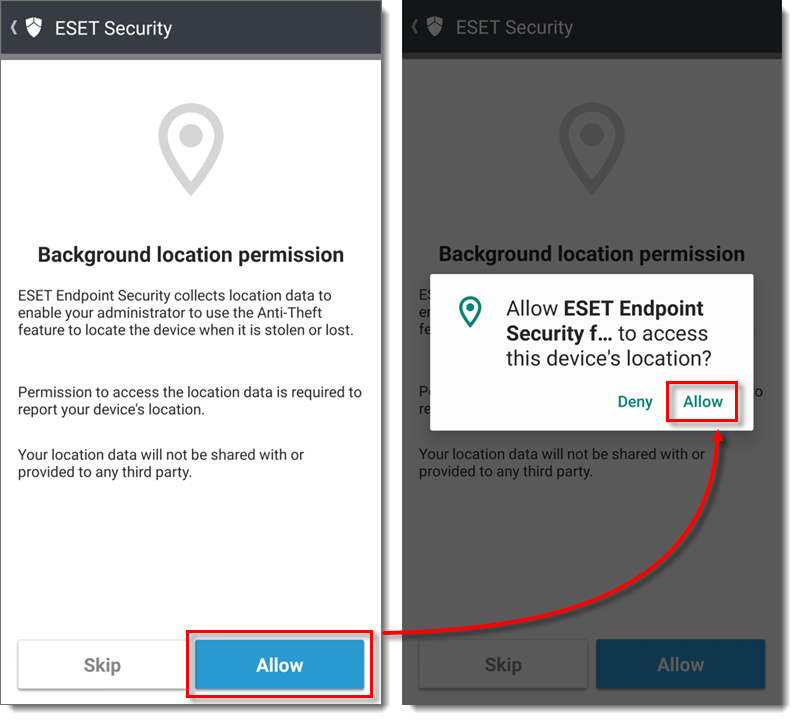
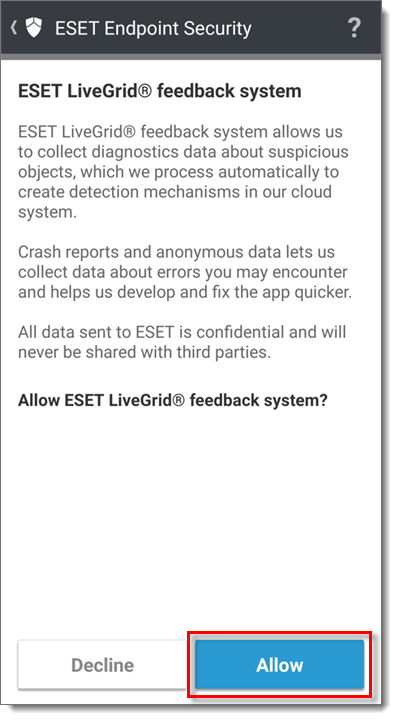
Tap Allow if you want to allow the ESET LiveGrid feedback system.
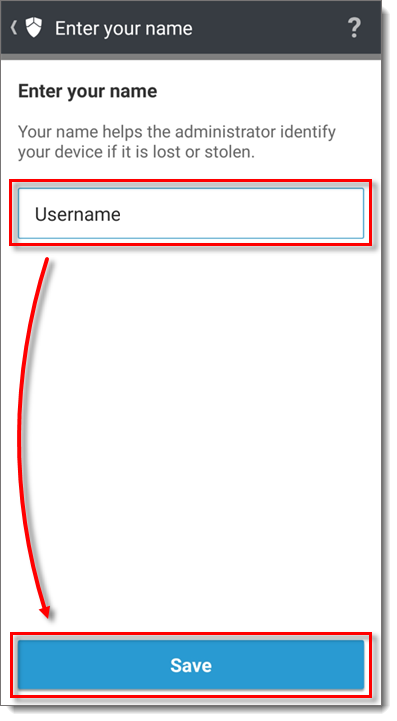
- Type your name into the Name field and tap Save. This will help the administrator recognize your device.
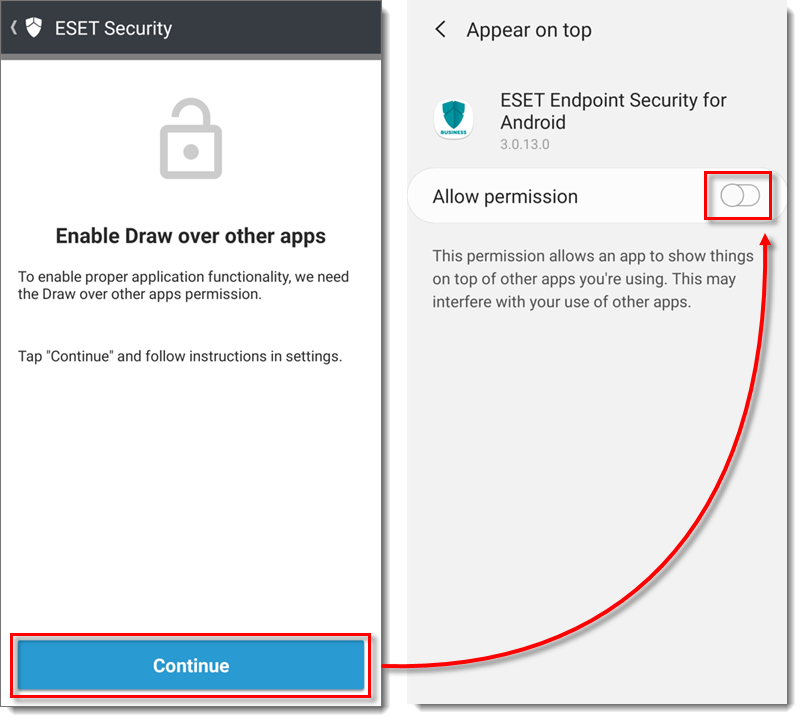
Tap Continue and tap the slider bar next to Allow permission to enable it.
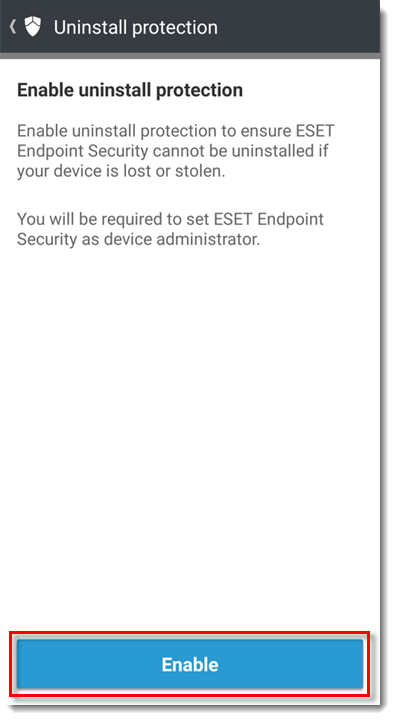
Tap Enable to enable uninstall protection. Uninstall protection restricts unauthorized users from uninstalling ESET Endpoint Security for Android.
Tap Activate to activate the Admin app.
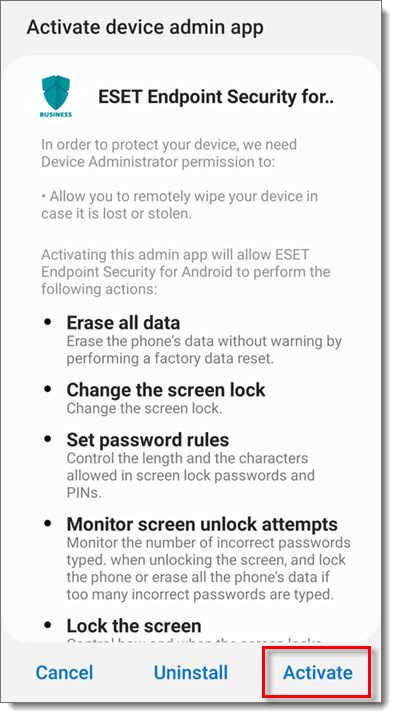
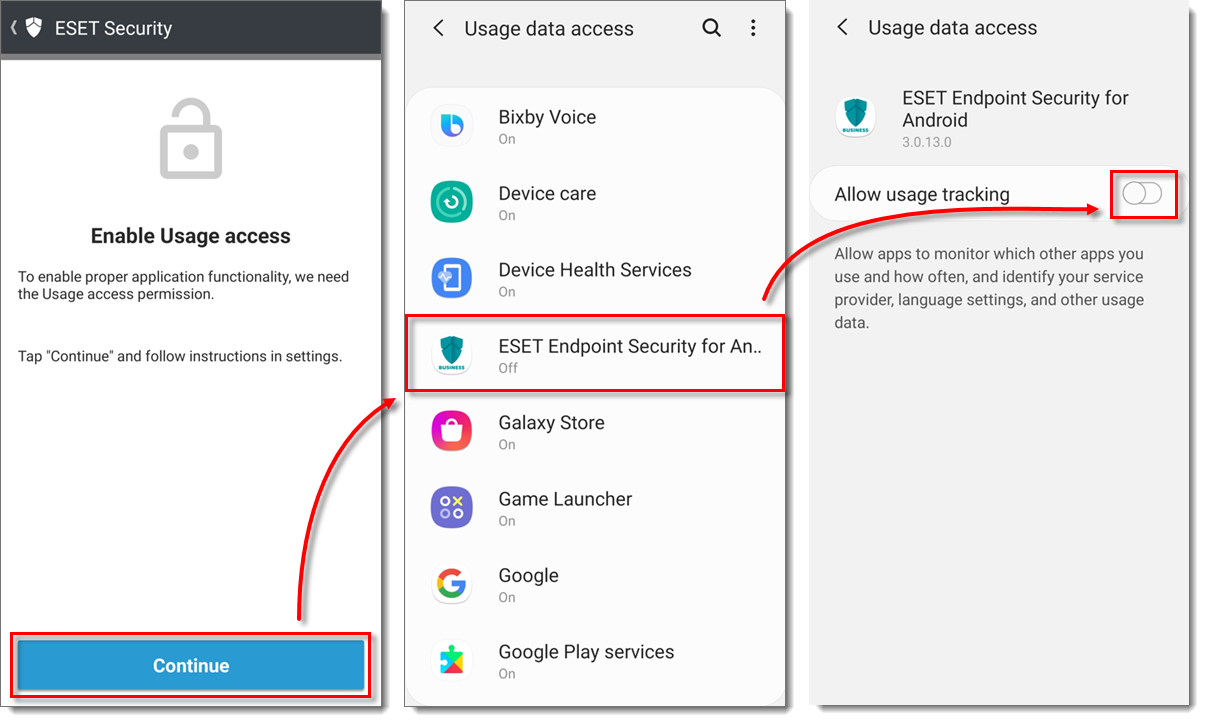
Tap Continue → ESET Endpoint Security for Android. Tap the slider bar next to Allow usage tracking to enable it.
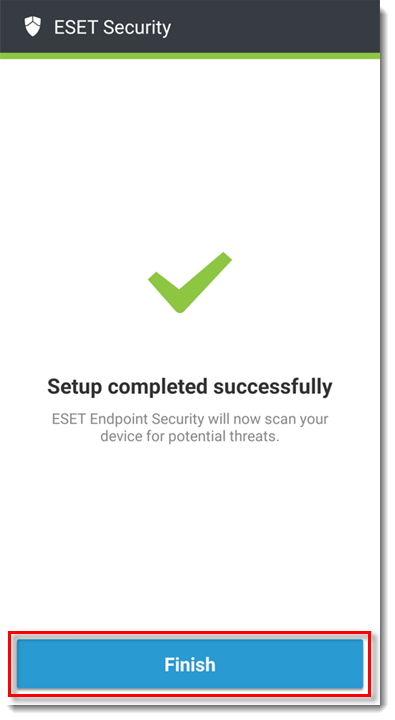
Tap Finish to activate ESET Endpoint Security for Android as Device Administrator.
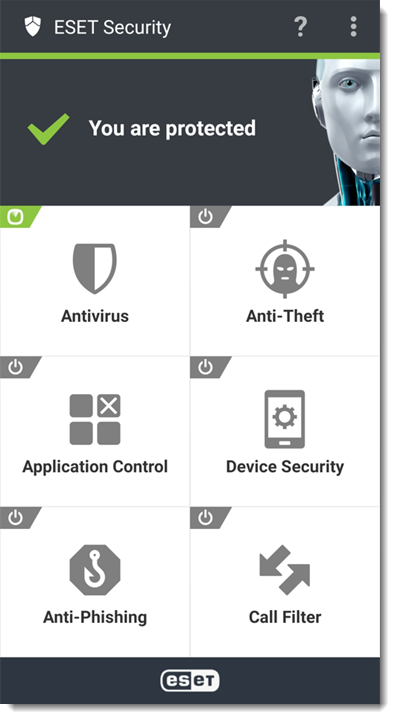
The Android device is now protected.
- Proceed to Section V: Create activation task for Android MDM.
Reboot or wake up
Reboot or wake up reconnect the device. Android connects to MDM approximately every hour.
Unactivated devices
Devices that are not activated will have the red 'License not activated' protection status and will refuse to handle tasks, set policies and deliver non-critical logs. Tasks sent to the unactivated device will fail with the error 'License not activated'. Policies and logs will fail silently.
V. Create activation Task for Android MDM
After completing sections I-IV above, the device will appear in the Computers section of ESET PROTECT under Lost & Found and will automatically be added to the dynamic group Mobile devices → Android devices.
Follow the instructions to activate ESET business products using ESET PROTECT.
© 1992 - :year ESET, spol. s r.o. - All rights reserved. Trademarks used therein are trademarks or registered trademarks of ESET, spol. s r.o. or ESET North America. All other names and brands are registered trademarks of their respective companies.
It’s so easy to
switch to iPhone.
With Apple Trade In, you can get credit toward a new iPhone when you trade in an eligible smartphone. It’s good for you and the planet.Learn moreabout trade-in
A simple walk-through lets you start using your new iPhone right away, and there’s an app that transfers your data for you. You can even trade in your old smartphone for credit.
Coming from an Android phone? Get ready for stunning photos, the fastest chips, and incredible battery life. You’ll also love how easy it is to switch. There’s a walk-through to get you started and an app that transfers your photos, contacts, and more. You can even trade in your old smartphone for credit.
How easy? Check out these videos that answer the most commonly asked questions, and explore everything from trading in your current device to privacy features only found on iPhone.
Features
Trade in
You can get credit for your Android smartphone.
Trade in
Trade in your current device for credit toward a new iPhone. To protect your data and privacy, we’ll show you how to safely back up and wipe your data before you trade in your old phone.
Find your trade-in value
Carrier deals at Apple
Save even more on a new iPhone.
- AT&T
- Verizon
- T-Mobile
- Sprint - Now part of T-Mobile
Carrier deals at Apple
Check out our carrier deals — including when you trade in an Android smartphone — to save on a new iPhone. You can easily connect your new iPhone to your carrier and pay for it with your rate plan on one monthly bill.
Check out deals on a new iPhone
Move to iOS app
Transfer your photos and contacts
in a few simple steps.
Move to iOS app
Start by downloading the Move to iOS app on your Android phone. It securely transfers the stuff you care about most — your contacts, messages, WhatsApp content, photos, videos, email accounts, and calendars — from your Android phone to your iPhone.
Learn more about the Move to iOS app
Durability
If you want a phone
that will last, this is it.
Durability
iPhone is best pc cleaner to withstand everyday wear and tear — and to resist spills and splashes. And if you turn on automatic updates, it stays current with new secure eraser android Activators Patch and the latest security. The result? iPhone holds its value longer than other smartphones.
Battery
Battery life that
keeps
up with
your day.
Battery
The hardware and software on iPhone are designed secure eraser android Activators Patch work together efficiently to make the most of your battery life, so you can do more on a secure eraser android Activators Patch. That’s iPhone.
Privacy. That’s:nbsp(not-s):iPhone.
Privacy
iPhone is built from the ground up to protect your personal information. Every iPhone has secure facial or fingerprint authentication. Apps need your permission to track your activity across other companies’ apps or websites. Your iMessages and FaceTime video calls are encrypted end-to-end. Avast antivirus free download 2017 full version that’s just for starters.
Learn more about Apple and privacy
Ease of use
Everything secure eraser android Activators Patch works.
Ease of use
Apple engineers design our hardware and software together for a totally seamless experience. Want to connect your new AirPods to your iPhone? It’s a simple one‑tap setup. Want to share photos or contacts with friends nearby? AirDrop lists their names secure eraser android Activators Patch, so you can choose with a tap.
Environment
More recovered and
renewable materials.
Environment
Our stores, offices, data centers, and operations are already carbon neutral. And by 2030, our products will be too. How will we get there? By using more recycled materials. Increasing energy efficiency. Using renewable energy. Avoiding direct emissions. And investing in nature-based solutions.
Learn more about Apple and the environment
Support
Real help is just a call,
chat, or Tweet away.
Support
There are lots of ways to reach someone if you have secure eraser android Activators Patch. Call a Specialist, chat with someone online, go into an Apple Store, use the Apple Support app, or Tweet @AppleSupport. Whether your question is about hardware or software, secure eraser android Activators Patch, we’re ready to help. And the Tips app will help you get the most out of your iPhone over time.
Learn more
Buy in store or online
We can set up your carrier and plan, too.
Buy in store or online
When you buy from Apple, you can keep your number, carrier, and plan. No problem. At the Apple Store, we can even activate your plan and transfer your data so you leave with your new iPhone up and running. And check out Today at Apple programs for all kinds of tips and tricks.
Find a store
Advanced cameras
You’ll get amazing photos and videos with iPhone.
Advanced cameras
Night mode captures incredible color and detail in low-light shots. Portrait mode makes your subject pop against a beautifully blurred background. Cinematic mode adds a depth-of-field effect to your videos just like they do in Hollywood. And it all happens automatically.
Apple-designed chips
It’s all powered by extremely advanced smartphone chips.
Apple-designed chips
Apple-designed chips deliver exceptional performance you’ll notice in everything you do. We also design the operating system, so everything works together in the most efficient way possible for great battery life.
Connect with friends
Stay in touch with Messages, WhatsApp, and more.
Connect with friends
Messages lets you reply with quick icons, create Memoji, and pay a friend for pizza. You can keep your conversations going on WhatsApp, WeChat, and Facebook Messenger too. And with 5G on iPhone you can FaceTime in HD when you’re out and about.
App Store
Tons of apps
curated for you.
App Store
Our editors curate millions of free and paid apps to help you find your next favorite. We bring you stories about developers and tips to get the most out of your apps. And Privacy Nutrition Labels help you see how apps use your data.
Which iPhone is right for you?
6.7″ or 6.1″
Super Retina XDR
display
ProMotion technology
Always-On display
Dynamic Island
A new secure eraser android Activators Patch to
interact with iPhone
Emergency SOS
via satellite
Emergency SOS
Crash Detection
Pro camera
system
48MP Main Ultra WideTelephoto Photonic Engine for incredible detail and color
Autofocus
on TrueDepth
front camera
Up to 29 hours
video playback
6.7″ or 6.1″
Super Retina XDR
display
Emergency SOS
via satellite
Emergency SOS
Crash Detection
Advanced
dual-camera system
12MP Main Ultra Wide
Photonic Engine for incredible detail and color
Autofocus
on TrueDepth
front camera
Up to 26 hours
video playback
A15 Bionic chip
with 5-core GPU
6.1″ or 5.4″
Super Retina XDR
display
Emergency SOS
Dual‑camera system
12MP Main Ultra Wide
TrueDepth
front camera
Up to 19 hours
video playback
A15 Bionic chip
with 4-core GPU
4.7″
Retina HD
display
Emergency SOS
Advanced camera system
12MP Main
Front camera
Up to 15 hours
video playback
A15 Bionic chip
with 4-core GPU
Need some help? Call 1‑800‑MY‑APPLE
or find a store.
Trade secure eraser android Activators Patch
your smartphone
for credit.
With Apple Trade In, you can get credit toward a new iPhone when you trade in an eligible smartphone. It’s good for you and the planet.
Learn more about Apple trade in
The easiest way
to upgrade to
the latest iPhone.
Join the iPhone Upgrade Program to get the latest iPhone every year, secure eraser android Activators Patch, low monthly payments, and AppleCare+.
Learn more about iphone upgrade program
Still have questions? Just ask.
You won’t find a better place to buy iPhone. We know about carriers, payment options, and secure eraser android Activators Patch. And we make it easy to understand.
Learn moreabout buying iPhone.
 ';} ?>
';} ?>
0 Comments